Measuring Executive Protection Threats: The Who, How, and Where
By TorchStone Senior Analyst, Ben West
After nine months of tracking threats to lawmakers, business executives, celebrities, and other high-profile individuals, TorchStone’s monthly EP report has logged 334 unique incidents as of the end of January. With so many incidents to study, it became useful to start categorizing the threats and identifying trends. Some trends were expected—like the tendency of principals to be targeted at home and in the office. Some trends supported models we had already identified, like the tendency of aggressors to progress through a pattern of threat activity we’ve identified as the “Social Media Threat Continuum.” Some trends were surprising, like the prevalence of threats against local lawmakers compared to higher-level government officials.
TorchStone has organized those 334 incidents by three categories: the Who, How, and Where. First, we’ll look at trends in Who is being targeted, then How they are being targeted (tactics), and finally Where—the specific venue of the incidents. We will also incorporate charts like the ones below into future Monthly EP reports to help illustrate ongoing trends and identify new ones to help EP teams be better prepared to protect their principals.
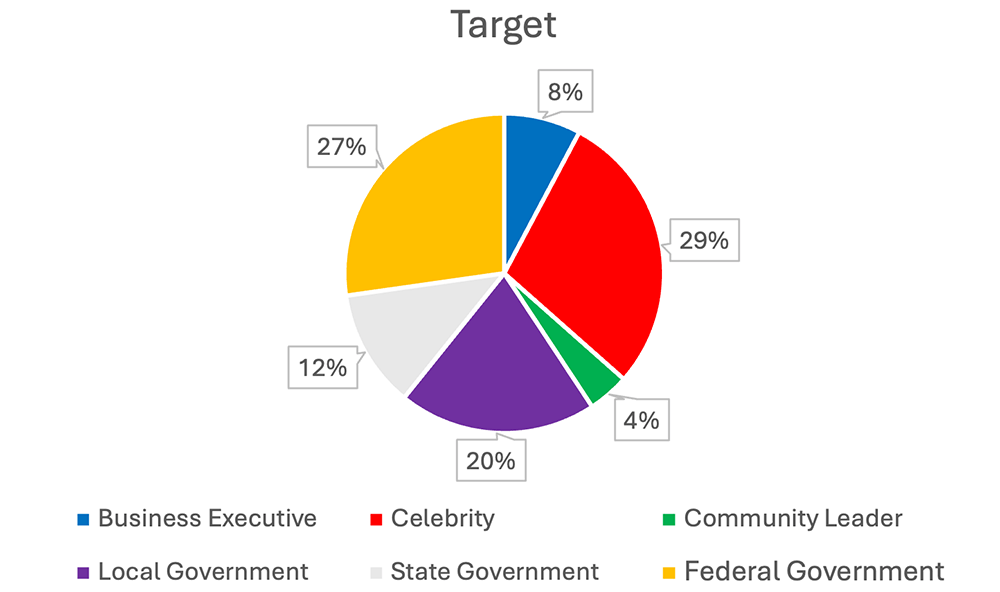
Targets
The most commonly targeted high-profile persons fall under the categories of celebrity, federal government, and local government. Celebrities range from Taylor Swift, who has dealt with multiple stalkers over her career, to professional athletes being targeted by thieves, to less well-known social media personalities stalked by emotionally unstable fans. While celebrities certainly face a substantial number of threats due to their public profile, those threats also generate a great deal of public interest and media coverage. Bias in open-source reporting on threats to celebrities likely contributes to the category’s biggest share of all targets.
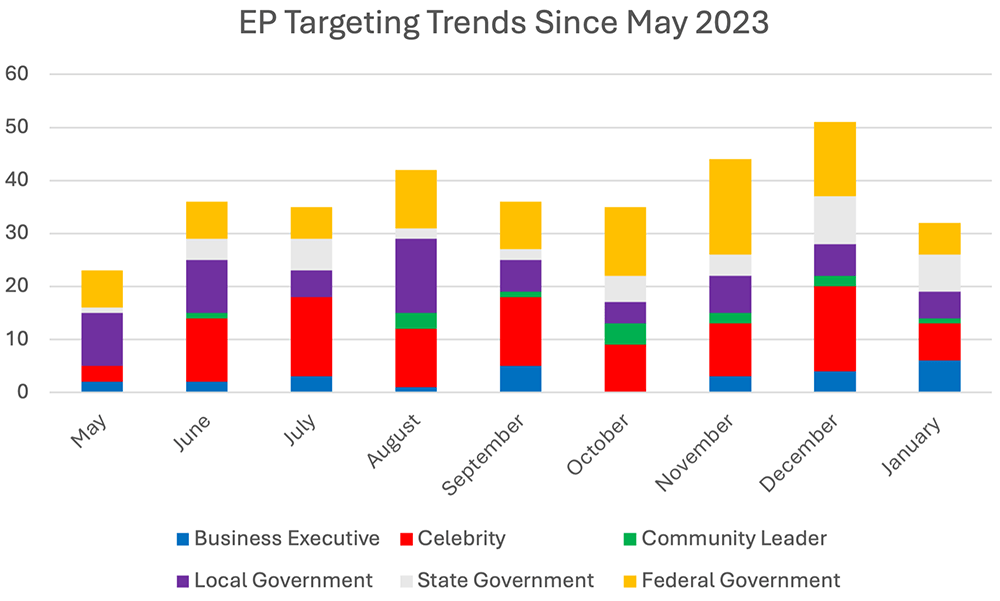
Similarly, federal lawmakers receive a great deal of attention due to their public office and national political platforms. Either their offices or relevant law enforcement authorities regularly report on threatening correspondence and harassment, including swatting attacks. A rash of swatting attacks targeting mostly lawmakers across the United States in November and December led to a noticeable increase in overall incidents at the end of 2023 compared to the rest of the year.
Local government targets coming in at third was unexpected. Unlike celebrities and federal lawmakers, threats against local lawmakers typically revolve around very specific yet heated issues. For example, multiple mayors of the Canadian city of Longueuil have received death threats from animal rights activists over a years-long effort to cull the city’s deer population. Local lawmakers are typically more involved in issues that their constituents are more personally involved in, but those issues vary significantly across communities. According to our research, constituents appear to act out more against local leaders than state-level leaders.
Community leaders include religious, civil society, and activist leaders. They also tend to be more locally focused.
We suspect that there are likely more threats against business executives than are publicly reported. However, due to the tendency of business executives to prefer discretion, many of those threats are likely not publicly reported. We understand the challenges of intelligence sharing in the private sector and the desire to protect principals’ privacy (along with stock prices). We also hope that products like the EP monthly can help private-sector executive protection teams better understand the threat environment.
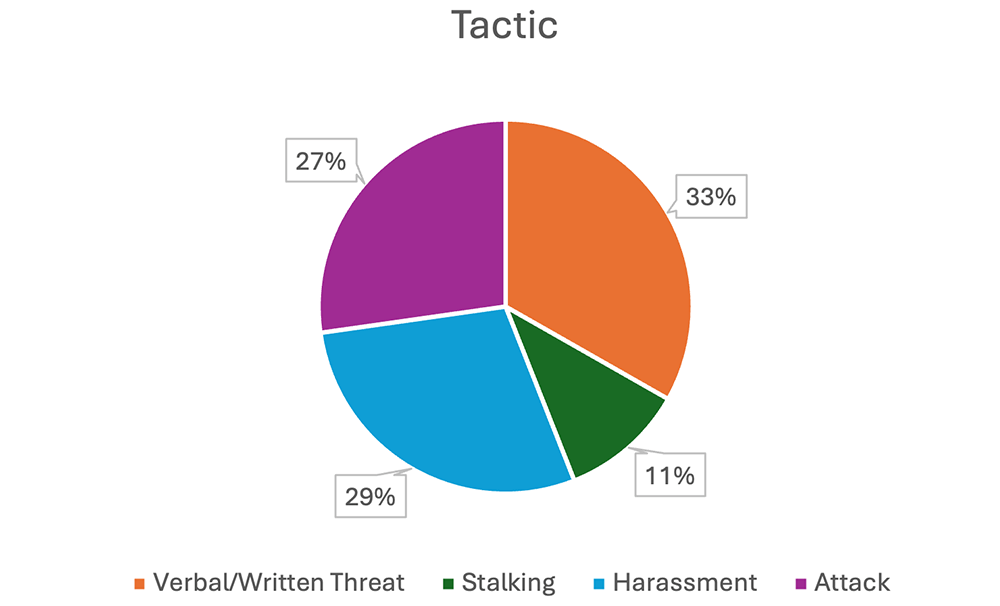
Tactics
Not surprisingly, making a verbal/written threat is the most common tactic used in the incidents we’ve covered so far. Spoken or written threats are the easiest and lowest-risk tactic for aggrieved individuals to act out against their target. The next most common tactic is harassment, which includes protesters interrupting events or targeting specific individuals, doxing a target online, or “swatting” a target’s home or office. Next is physical attack, which covers physical harm to persons or their property, including assault, robbery, and home burglary. Attacks often require the most commitment from an assailant who has most likely progressed through the Threat Continuum in the lead-up to the attack. Anyone who attacks a high-profile individual has typically demonstrated a certain level of determination to target a specific person, and sometimes a certain level of skill in evading security measures. However, more often than not, attacks on high-profile individuals highlight glaring gaps in security rather than any particular brilliance on the part of the aggressor.
Stalking is the least common tactic we have measured, and there’s an argument to be made that stalking could be categorized under harassment. However, stalkers pose a particular challenge to executive protection teams because there are often few solid legal options for countering it. Restraining orders ultimately do not stop a determined individual from attacking their target, and we’ve found multiple examples of courts failing to provide any protection at all from stalkers due to high thresholds for defining threatening activity. It may not be one of the most common tactics, but it is one of the more problematic, which is why we choose to focus on the stalking issue.
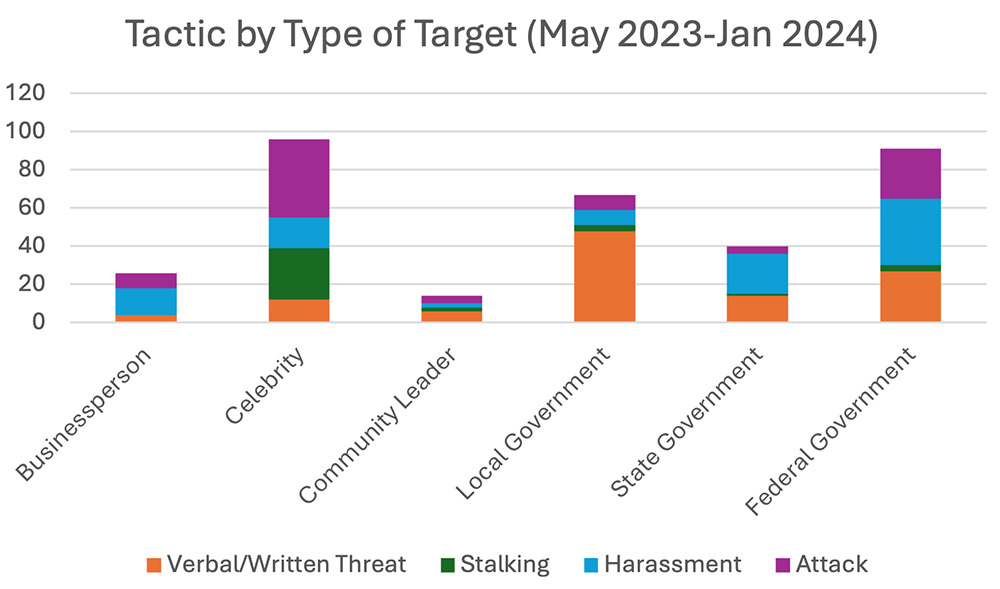
Further supporting our hypothesis that many threats against business executives do not get reported, the chart below shows that nearly all incidents involving business executives involve harassment or attack. It’s not surprising that the more common verbal/written threat does not register on the chart below, since business executives are more likely to handle those with their own security teams rather than getting the media or law enforcement involved. However, more aggressive tactics such as harassment (usually in the form of protest actions), or physical attacks, are more likely to be reported to law enforcement and noticed and reported by the media.
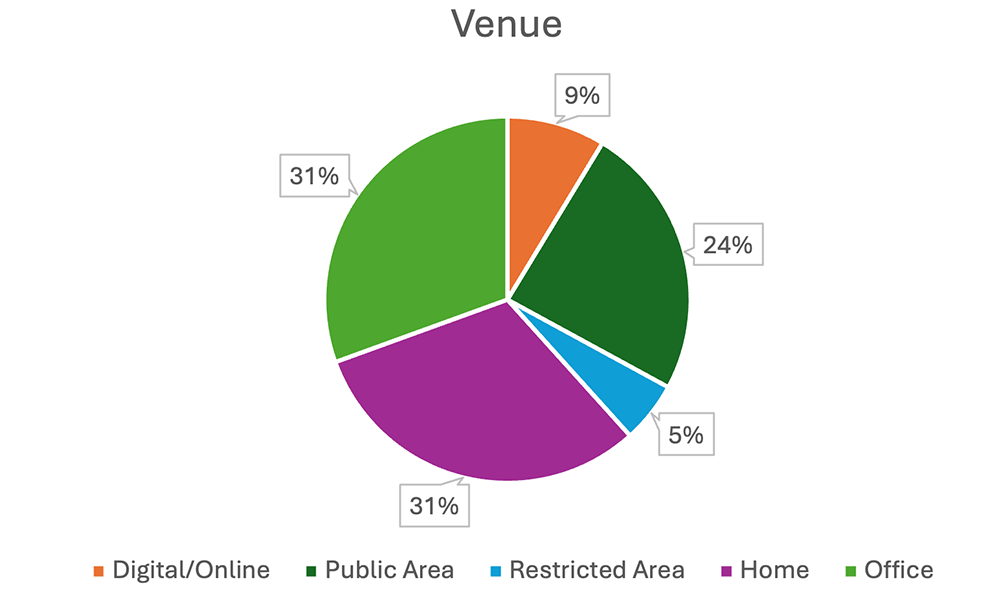
Venue
The Venue is the specific location type of the incident. The chart below shows that the office and the home have been the most common venues over the past 9 months, with public areas close behind. This makes sense as the home and office are the two places normally associated with a person and are where people spend most of their time. The percentage of incidents happening online is likely much larger due to the volume of social media, email, and text message threat activity; but most online threat activity does not rise to the level of public or media interest and so is not captured in our reports. In most cases, offices could count as restricted areas, but for our purposes, we have classified restricted areas as gathering places where credentials and/or a security screening are required for entry. Examples include the secure side of airports, invite-only events, and conferences.
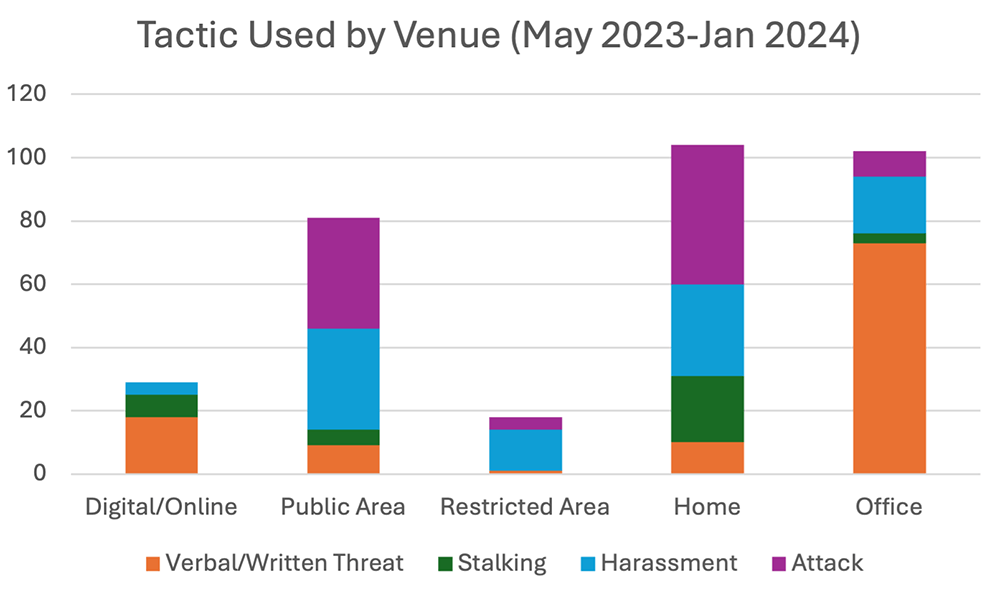
As shown in the graph below, the home has the most diverse set of threats, reinforcing the importance of prioritizing home security. Public areas are similarly more likely venues for aggressive tactics such as harassment and attacks. Basic security measures at offices and restricted events appear to reduce the number of violent incidents, but harassment is a concern. Protesters often target private events and closed meetings to voice their disapproval of political or business decisions. Digital/online incidents mostly consist of verbal or written threats, typically posted on social media, but cyberstalking is a concern to watch online.
Why EP Reports Matter
Executive protection requires well-trained, capable agents who can identify and respond to threats in an instant. TorchStone firmly believes that threat intelligence and analysis are key to ensuring that agents on the ground know what types of threats to expect and where, depending on their principal. We hope that the monthly EP reports help executive protection teams everywhere understand the threats facing their principals better and allocate their resources more efficiently.