Preparing for the Next Swatting Attack
By TorchStone Senior Analyst, Ben West
The recent Christmas and New Year holidays saw a wave of swatting incidents targeting local, state, and federal lawmakers and judges—as well as some of their family members and high-profile political donors. Some swatting targets, like U.S. Representative Marjorie Taylor Greene, had been targeted in multiple previous hoaxes. Others, like progressive political donor, George Soros, had been targeted in similarly disruptive bomb hoaxes. The wave of incidents capped off a year in which lawmakers reported feeling increasingly at risk due to threatening phone calls, emails, and letters.
It should not come as a surprise that increasingly threatening communications eventually resulted in harassing swatting attacks. TorchStone has placed swatting in the context of the “Social Media Threat Continuum,” a scale of increasingly aggressive behaviors that aggrieved individuals use against their targets. By understanding the model, individuals can better understand if they are at risk of swatting (or other similarly harassing actions) in the future. Taking proactive steps to prepare for swatting attacks can greatly mitigate their impact.
Understanding The Motivations Behind Swatting
Swatting has been around since at least 2008 and it targets hundreds of homes, schools, government offices, and businesses every month. Swatting is a particularly sinister form of harassment since it misleads local police forces into thinking that there is a life-or-death emergency occurring at a particular location, frequently causing them to respond with deadly force. In the best-case scenario, police waste valuable time and resources responding to a hoax call but in the worst case, innocent people can die. In 2017, a father of two was shot and killed by police officers responding to a swatting call claiming there was a hostage situation at the victim’s home. Authorities eventually caught up to the hoax caller, based in California, and tracked him to at least 50 other swatting incidents targeting people across the country. Many of those incidents were motivated by disputes with people in his online gaming community.
Like other forms of harassment and physical attacks, swatting does not occur in a vacuum. As noted in the examples above, many of the most recent victims of swatting over the holidays had been targeted before—either in previous swatting attacks or through other forms of harassment. TorchStone has previously written about the “Social Media Threat Continuum” as a model for understanding how aggrieved individuals can escalate the severity of tactics used against their targets. Swatting (along with bomb hoaxes and vandalism) is a form of harassment that typically follows several less aggressive targeting tactics.
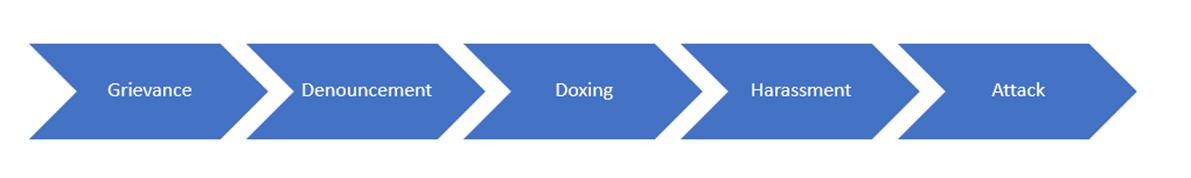
Social Media Threat Continuum
While an aggrieved person can skip the first three phases and jump straight to harassing their target, it is far more likely that they will first provide warning signals of their intent by voicing their grievance, denouncing their target, and using tactics such as doxing to intimidate their target. If these do not generate the desired results for the aggrieved person, harassment is the next phase.
Targeted individuals who are paying attention should not dismiss a person or a group that voices grievances against them or denounces them—publicly or privately. Such signals are important indicators of the potential for more serious threats to come—such as swatting, or even physical attacks.
While the most recent wave of swatting attacks over the holidays appears to be motivated by political disagreements, grievances for swatting attacks can range from romantic rejection to financial rewards.
In November 2023, police arrested a California man after he carried out multiple swatting calls and hoax bomb threats at schools and other locations in Pennsylvania. Investigators determined that the suspect made the hoax calls as a continuation of a stalking and harassing campaign targeting an underage girl he had met online.
Also in November, Pennsylvania police were able to identify the suspect behind a series of swatting calls targeting a specific residence based on comments he had made on his social media page. While the exact details of his comments were not made public, reports suggest that he had a grievance against someone at the residence, illustrating the link between posting online grievances and harassment.
Another recent swatting suspect was motivated by financial rewards and receiving pornographic images. Prosecutors in Washington state indicted a man on charges of carrying out 20 swatting calls against targets in 11 U.S. states and two Canadian provinces from June – September 2022. The suspect leveraged stolen personally identifiable information available on dark web platforms to identify his targets. He would then contact them, threatening to swat their residence if they did not give him money or sexually explicit photos. He appears to have contracted out his services as a kind of “swatting mercenary,” even livestreaming his exploits on Discord to gain popularity.
Such serial swatters are high priorities for law enforcement, as they appear to be responsible for most of the swatting attacks that occur.
Mitigating the Swatting Threat
Sophisticated swatters are difficult to track down and catch. They use special anonymized calling software and services to disguise the location of their call. They also often distribute swatting calls over localities throughout the United States and Canada to avoid recognition further. Until recently, there wasn’t a central database for capturing the details of such calls, but in June, the FBI established a national swatting database to start identifying patterns of swatting activity. As seen in some of the examples listed above, most identified suspects have been serial swatters, using the same tools and sometimes even the same scripts to target dozens of victims over a short time span. Databasing these incidents and sharing their details with police departments and 911 dispatchers should help them identify future swatters based on certain call signatures, keywords, and timing of their calls.
However, individuals should still take measures to mitigate the threat of swatting attacks against their homes, schools, offices, and places of worship.
First, assess whether you, your family, or associates are likely to be targeted in a swatting attack. The “Social Media Threat Continuum” mentioned above can go a long way in determining the current threat of swatting or other forms of harassment. If an individual knows that there are people or groups with grievances against them, that those groups have denounced the individual, and that the group has used swatting to target other people, they should consider themselves at high risk of being swatted themselves. Awareness of the potential for swatting can help them take steps to mitigate the threat.
Second, potential swatting targets should coordinate with local law enforcement to ensure they understand the possibility of receiving swatting calls targeting a residence, school, office, or place of worship. As swatting has become more common, 911 dispatchers are becoming more aware of the tactic and are more likely to pay attention to warnings provided by potential victims. This will provide dispatchers and first responders with context that will help them adjust their response should there be a 911 emergency at the residence. Potential targets should also prepare themselves for the eventuality of a swatting attack and be ready to cooperate with police if they do show up as the result of a hoax phone call. Potential targets must understand that police are likely to treat a situation as hostile based on the information they have received. If the residents cooperate and do not escalate the situation, it is likely to be resolved more quickly and with less risk of harm to anyone involved.