-
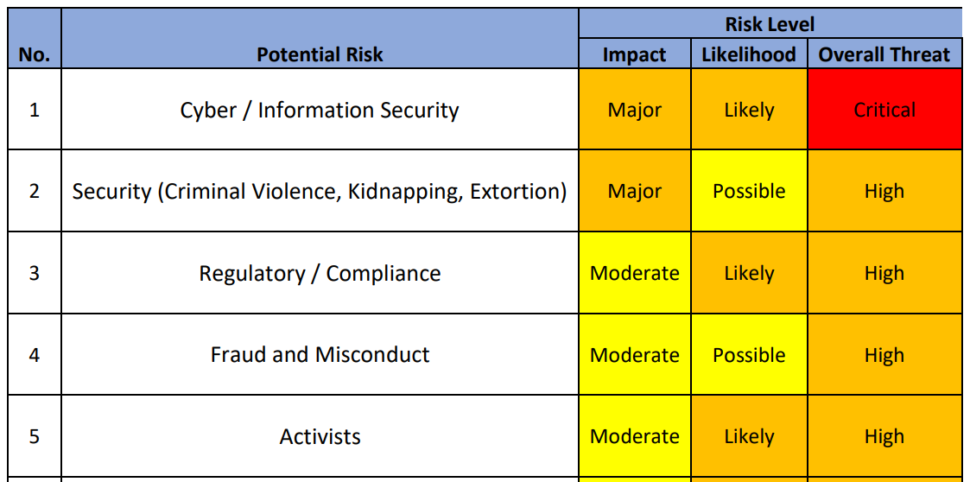
Understanding and Responding to Risk
Read moreEverything an organization does or does not do brings a risk. It is impossible, and one should not try, to…
-

Don’t Overlook the Threat Posed by Bugs
Read moreWhile a lot of attention and budget is currently being devoted to cybersecurity—and justly so—cyberattacks are just one of the…
-

Reporting Bombmaking Activity Can Save Lives
Read moreAmateur bomb makers who have not received any training typically progress along a learning curve, becoming more proficient at their…
-

Detecting Hostile Surveillance
Read moreAttacks and other crimes don’t just appear out of a vacuum. They are the result of the attack cycle and…
-

Avoiding the Deadly “Oh-Oh loop” with OODA
Read moreThe process of consciously observing, orienting, deciding, and acting—the OODA Loop—creates links between an awareness of one's surroundings in a…
-

The Enemies of Situational Awareness
Read moreAs I wrote a few weeks ago, situational awareness is simply paying attention to what is happening in the environment…
-
Narcotica podcast discusses Mexico’s rise as a narco state with TorchStone’s Scott Stewart
In Blog, Corporate Security onRead moreDuring the height of the drug war’s surge under Ronald Reagan and George H.W. Bush, Scott was assigned to protect…
-

Beijing braces for perfect storm of Olympic woes
In Blog, Corporate Security onRead moreBeijing 2022 Olympic Winter Games will take place not only under the shadow of Covid-19, but as the most politically…
-
Unconventional Security for Unconventional Clients
Read more“Old money” families have had generations to learn about the dangers associated with vast wealth and the security measures required…
-

How to Practice Sustainable Situational Awareness
Read moreSituational awareness is simply paying attention to what is happening in the environment around you in an effort to identify…
CALL US: (877) 897-6428
