
Mail-Based Threats: Analysis and Management
By TorchStone Senior Analyst, Ben West
How to Manage Mail-Based Threats
Parcel threats come in many forms, ranging from sophisticated explosive devices, envelopes containing lethal substances, or the more common written threat against an individual or organization.
Even in the 21st century, parcel delivery services are a common vector for threats due to the anonymity they can provide the sender and the low cost of reaching a target thousands of miles away.
In this edition of The Watch, we assess recent parcel threat campaigns and provide general guidance for how organizations can assess and mitigate threats they face through the mail.
We also emphasize the intelligence value of monitoring, preserving, and databasing mail-based threats in order to anticipate and avoid future threats.
Still a 21st-Century Threat
Between Nov 24 and Dec 1, Spanish authorities and security personnel discovered six devices containing explosive material addressed to various targets in Spain—including a private company in the defense industry.
Only one of them, a parcel addressed to the Ukrainian ambassador to Spain, detonated, slightly injuring a security officer at the Ukrainian embassy in Madrid.
The other five devices targeted Spanish government offices, the US embassy, and a Spanish weapons manufacturer that made ordnance that NATO supplied to Ukraine in its war against Russia.
Ukrainian officials noted their diplomatic missions around the world, from Kazakhstan to the United States, had received at around the same time other forms of threatening mail, including ominous blood-soaked packages and animal parts.
In late January, Spanish authorities raided a residence in northern Spain where they found tools consistent with the parcel bombs.
They arrested a 74-year-old retiree whom they accused of having links to Russia, but no further details are available due to the sensitivity of the case.
The Spanish retiree was neither the first nor will he be the last to employ parcel bombs as a tactic.
The ability of this most recent campaign to get harmful weapons into sensitive areas and attract global media attention highlights the appeal of mail threats to those wanting to harm or intimidate a victim.
Mail threat campaigns have been a persistent tactic by individuals motivated by political and personal grievances or even financial gain.
Greek anarchists and anti-government elements carried out a years-long mail threat campaign that targeted offices of Greek government officials, European political leaders, and financial institutions following the Greek financial crisis in the early 2010s.
In 2017, that campaign resulted in the serious injury of a secretary for an IMF official in Paris.
In 2018, a supporter of then-President Donald Trump mailed incomplete pipe bombs to prominent critics of the Trump administration, including billionaire George Soros, Barack Obama, and Hillary Clinton.
While there were no injuries associated with that campaign, it did generate significant disruptions in the form of building evacuations and fear.
A Weapon for Publicity
Unlike active shooters, parcel bombing campaigns are rarely lethal, but what they lack in lethality, they make up for in terror and disruption.
Even if a parcel bomb does not detonate, it can force the evacuation of a midtown Manhattan skyscraper—as in 2018, when the Time Warner Center in New York evacuated after CNN received a parcel bomb at its offices.
The longevity and the (sometimes) unpredictability of parcel bomb campaigns can capture public attention and increase fear to publicize a message—whether it be opposition to NATO’s support for Ukraine, criticism of economic inequalities, political disagreements, or simply personal grievances.
Whereas mass shootings are typically over in a matter of minutes and oftentimes result in the shooter’s death, parcel bombers almost always survive their attacks and can use their weapons to mount campaigns that go on for days – even years – in order to maximize the publicity towards the attackers’ grievance or inflict terror in the victims.
Parcels do not have to contain bombs to be lethal or disruptive: packages containing poisonous substances such as anthrax, ricin, other biological and chemical weapons, or even substances resembling those materials can similarly force an evacuation, cause injuries, or even death.
While the campaign of envelopes containing anthrax in the fall of 2001 that killed 5 and injured 17 was highly unusual, individuals mailed envelopes filled with white powder to intimidate targets on a regular basis.
In late February 2023, a local administrative office in Wilkes-Barre, PA required an emergency response and partial evacuation after reports of a suspicious letter containing white powder.
Authorities eventually cleared the scene and determined that there was no threat, but the incident still caused considerable disruption to businesses and personal lives.
Managing Parcel Threats
While every employee should recognize the signs of a suspicious package, organizations can mitigate the disruptive impact of suspicious packages through proper mail-handling processes.
Mailroom safety strategy can be implemented as well as how individual personnel can avoid and contain parcel threats.
The first step of any new security policy should be to assess the threat.
Organizations should assess the volume of mail they receive, review their history of parcel threats, and consider whether they could be targeted in the future.
Organizations in the public, financial, defense, and legal sectors are among the most targeted, but no organization is immune to controversy or personal grievance that could evolve into a disruptive or destructive threat.
The nature of the threat should determine the next steps.
In more extreme cases, organizations should consider establishing a mail processing facility separate from their main offices so that in the case of a threatening parcel arriving, disruptions can be contained to an off-site location disassociated from the main offices.
If an off-site facility is not possible, then organizations should consider installing a stand-alone mail processing unit, preferably a small structure with some stand-off distance from the primary building that can be quickly sealed in the case of a threat.
Many organizations use modified shipping containers so that in a worst-case scenario, the container could simply be sealed up and towed away.
If an organization does not have a separate mail screening facility or should a parcel threat make it through screening, employees must know the basics about handling suspicious parcels.
Letters from an unknown or unidentified source warrant closer inspection.
If the receiver wasn’t expecting a particular parcel, he or she should briefly inspect it, looking for the following indications that the parcel could be a threat:
- Addressed to a generic office (e.g. CEO) or well-known individual within an organization.
- Excessive postage to ensure the package arrives.
- Unusual notations or instructions on the exterior.
- Lumpy, rigid, or otherwise misshapen packages indicate unusual contents.
- Discoloration, grease stains, or strange odors on the parcel suggest volatile chemicals inside.
- Finally, wires or other unusual protrusions from a parcel are an immediate indicator of a threat.
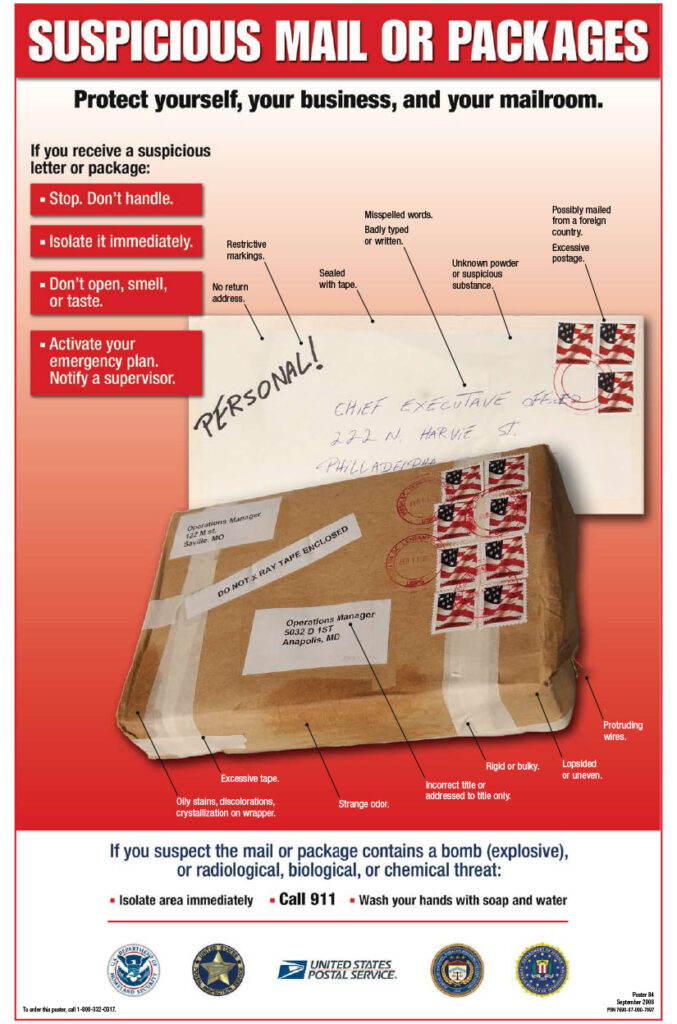
Source: USPS (https://about.usps.com/securing-the-mail/suspiciousmail.htm
If any employee notices any of these features about a parcel or has other reasons to be concerned about the contents of a parcel, they should set it down and clear the immediate area.
Preferably, they would set it on the floor, potentially under a desk or a wastebasket, and close the door behind them to contain the impact of the contents of the parcel.
Harvesting Intelligence from Mail-Based Threats
Finally, organizations should keep track of parcel and bomb threats (along with electronic, phone, and in-person threats) to identify individuals or trends of particular concern.
Threats rarely materialize out of thin air.
They tend to build up over time and are noticeable if someone is paying attention.
Persons with a grievance against an organization will frequently communicate their anger in some form before resorting to violence and letters are a common medium for expressing that anger.
The use of threatening language or the inclusion of threatening objects is cause for concern.
Preserving and databasing threatening or even critical correspondence is key to identifying the most likely source of future threats and avoiding them.
