
Kidnapping Part 6: Crypto Kidnapping
By TorchStone VP, Scott Stewart
The man who answered the doorbell of his upscale Madrid residence was expecting a lady..
Eagerly, he unlocked the door.
As he swung the door, it suddenly slammed open and a group of four men barged through it, sprayed him in the eyes with pepper spray, and quickly handcuffed and blindfolded him.
The four intruders spoke with Eastern European accents and addressed each other using only numbers.
Quickly, they used items of clothing to cover the security cameras in the residence and moved their subdued victim to his home office.
They moved with an efficiency that indicated they were professionals executing a carefully scripted plan.
Once they secured the victim in his office, they began to demand the keys to his cryptocurrency accounts.
When he refused to provide the demanded information, the men beat him, jolted him repeatedly with a taser, and even sliced his chest with a knife to force his compliance—a process that lasted several excruciating hours before the victim finally relented.
While the men did take bags of valuables they had ransacked from the residence as they left, their real goal was access to the victim’s cryptocurrency accounts, which reportedly contained some $58 million.
The man had become the latest in a long line of crypto kidnapping victims, and he was lucky to be alive—other crypto kidnapping victims had not been so fortunate.
Crypto Kidnapping
In most traditional kidnappings for ransom, someone valued by the target of the crime is abducted and held hostage until the target pays a ransom.
Often the person abducted is a child of the target, hence the name kidnapping.
But in a crypto kidnapping, the person abducted is also the target of the abduction and is forced to pay their own ransom by surrendering the keys to their digital cryptocurrency account.
In this way, a crypto kidnapping can be similar to many express kidnappings where the victim is held, and their bank account drained using a bank card.
But in crypto kidnappings, the stakes are often far higher than express kidnappings, with the targeted crypto accounts potentially holding millions of dollars.
Because of this, crypto kidnappings are often conducted by professional criminals who tend to be more sophisticated than the street thugs commonly involved in express kidnappings.
These criminals will often use high-level tradecraft that is more akin to that of kidnappers for ransom to identify and select their targets, as well as to surveil the target and execute the abduction.
Also, due to the high stakes involved, the criminals conducting crypto kidnappings will often use firearms, even in places where firearms are uncommon, like the UK.
As seen in the example above, the kidnappers are often willing to be quite brutal in extracting the information they need to seize control of the cryptocurrency accounts.
In 2019, a cryptocurrency trader in the Netherlands was beaten, waterboarded, and even tortured by having holes bored into his body with a power drill during a crypto kidnapping. Other victims have been burned with hot irons on sensitive parts of their bodies.
Crypto Kidnapping Attack Cycle
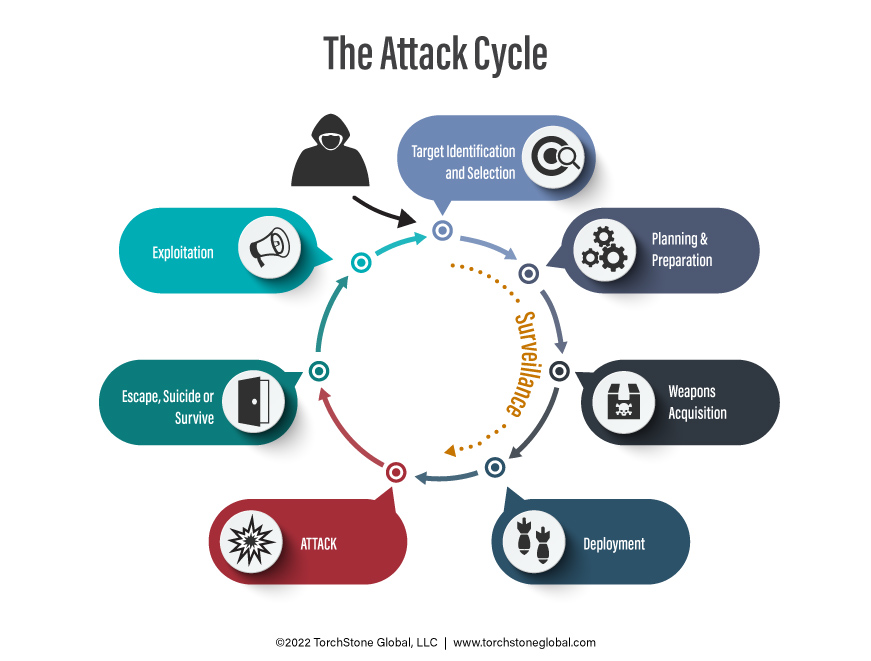
The attack cycle for a crypto kidnapping is often a complex one.
Criminals first need to identify a potential target.
Given the nature of cryptocurrency trading, it can be difficult to identify the large holders of a given currency.
Because of this, the criminals must often wait for the traders to identify themselves by boasting in crypto chatrooms or message boards, or other social media outlets.
Tracking down the location of the targets can also be a challenge since many crypto traders don’t report to a known business address.
Instead, many crypto traders work at home, and some of them are itinerant and work from several locations that can even be in different countries.
Only after the target has been identified, selected, and located can the planning portion of the attack cycle begin.
Often crypto kidnappings will focus on the target’s residence.
This is because the residence is often where they both live and work and thus spend most of their time.
Computers, external drives, and other materials may also be kept in the home office which can help in getting access to the victim’s crypto accounts.
In cases where a crypto kidnapping has happened on the street, someone will often have to go to the victim’s residence to retrieve a computer or other item to complete the theft transaction.
This was seen in a 2017 crypto case in New York in which the suspect arranged for the target to be abducted after a meeting in a Restaurant near Times Square.
After the victim provided the kidnappers with the information they needed, they still had to travel to the target’s home to retrieve the memory stick that contained his digital wallet.
Malice Aforethought
Planning a crypto kidnapping involving an abduction at the residence is like planning a home invasion robbery or tiger kidnapping.
In such cases, the kidnappers will need to surveil the residence to determine the residential security measures in place and to plan the best way of entering the residence and subduing the victim.
To gain an understanding of residential security measures, the criminals may use inside knowledge gained from a household employee, or someone who has visited the residence.
It is not unusual for criminals to use a honeytrap involving prostitutes or other attractive young women to conduct surveillance on the residence.
The next step is to determine the target’s pattern of life so the attack can be launched when the victim is at home and preferably alone.
Honeytraps can also be helpful in collecting this information, or even in orchestrating the home invasion.
The criminals will also need to ensure that they will have access to the victim for a prolonged period in case it is necessary to use force to gain the victim’s compliance.
The criminals then need to plan how they will escape from the crime scene without being identified or captured and then be able to anonymously move and launder the cryptocurrency so that they can access it without being caught.
This can be more difficult than some criminals realize, and criminals have been caught by tracking crypto transactions.
Prevention
Like other kidnappings, I consider crypto kidnappings to be avoidable.
They don’t just happen but are the result of a complex planning process, and those planning them are vulnerable to detection as they progress through their attack planning cycle.
But beyond detecting preoperational surveillance or other attack planning indicators, perhaps the best way to avoid a crypto kidnapping is to hide the fact that one owns a large amount of cryptocurrency.
Many victims have been identified based on their social media posts.
One is likely to draw the attention of criminals to yourself if they post photos of themselves talking on a “money phone” on Snapchat.
Instead of such attention-drawing behavior, it is far better to “live gray” and avoid drawing attention to oneself, whether on the internet, while traveling, or when one is at home.
This may not always be possible for individuals who are known to run crypto companies, but most people who have invested in cryptocurrency are anonymous, and nobody will know of their wealth unless they reveal it.
Beyond discretion and maintaining a low profile, common sense personal security, proper situational awareness, and adequate residential security measures are also important protection against being targeted for a crypto kidnapping.
The idea is to make oneself a difficult target to attack so that the criminals will select another victim during their attack cycle.
Those with substantial crypto holdings can also take some practical steps to protect their accounts.
First, they can break up their holdings into more than one wallet and have one wallet that they are prepared to surrender to criminals in case of a crypto kidnapping.
Second, they can set up their accounts so that multiple passwords or signatures are required to access them and then store the two passwords separately.
Often the second password will be stored in a secure location such as a safe deposit box.
Using a physical device known as a “cold wallet” can also help protect crypto accounts from phishing and other hacking attacks.
However, it is possible for kidnappers to abduct a target, seize the cold wallet and force the target to divulge the password, so it is prudent to use multiple passwords/signatures even when a cold wallet is used.
Lessons Learned
It can sometimes be hard for a person who has acquired a great deal of wealth quickly to understand the security implications that come with a high net worth.
This is true for all entrepreneurs, not just crypto investors and traders.
But hopefully, the large number of past cases of crypto kidnappings will prove instructive in illustrating the need for an appropriate level of security to help prevent future attacks.
One final word.
If someone finds themselves kidnapped by ruthless professional criminals, it is better to cooperate and live than die or be significantly disfigured.
As in all economic crimes, one’s possessions are not worth one’s life.
This report is the sixth and final in a series addressing different types of kidnapping and their motivations. The first part of the series, Understanding Kidnapping Threats, introduces different types of kidnapping. The second part, High-Value Kidnapping for Ransom, discusses how the required complex planning can be an advantage. The third part, Express Kidnapping, explores how these kidnappings do not follow the typical attack cycle. The fourth part of the series, Virtual Kidnapping, considers who the real victim is. The fifth part, Tiger Kidnapping, addresses how kidnappers use their victim to commit a second crime.
