Where the Attack Cycle Intersects the Pathway to Violence
By TorchStone VP, Scott Stewart
I’ve written about how the concept of the attack cycle is a useful framework protective intelligence practitioners can use to understand, identify, and detect behaviors associated with an intentional or targeted attack. I’ve also discussed how the demands of the attack cycle require those planning an attack to conduct certain activities and the vulnerabilities to detection they leave themselves open to. Now I’d like to examine how the attack cycle intersects with another model for understanding the behavior and indicators assailants exhibit before an attack, known as The Pathway to Violence.
The Pathway to Violence
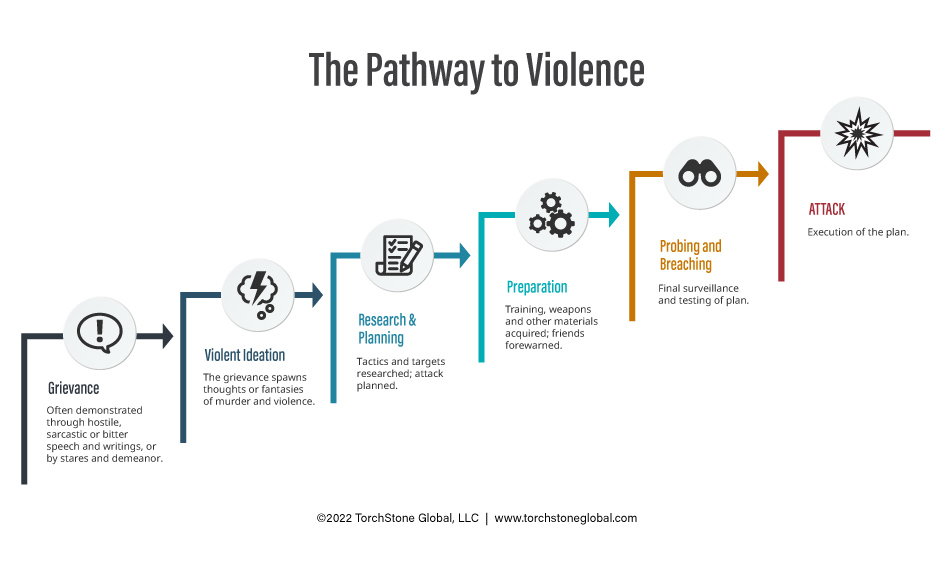
The concept of the “Pathway to Violence” was developed by Frederick Calhoun and Steve Weston in 2003. As I wrote in the piece on the attack cycle, people “don‘t just snap” and conduct a terrorist attack or other acts of targeted violence. Attacks are the result of a discernable process, a process Calhoun and Weston’s model divides into six steps.

According to this model, the pathway leading to an attack begins with a grievance. Some grievances are personal in nature, such as the termination of employment, playground bullying or romantic rejection. Other grievances can be more general in nature, such as the white supremacist narrative that whites are being replaced by immigrants, or the jihadist narrative that Islam is under attack by “Jews and Crusaders.” In many cases, assailants often embrace these general narratives, making them quite personal. Grievances can also start out as a personal issue that festers and later becomes part of a more general grievance narrative. For example, a man who struggles in his relationships with women and who then begins to view those rejections through the prism of the misogynistic Incel grievance narrative.
Grievances can be exhibited by hostile, sarcastic or bitter speech directed toward the person’s perceived enemies, known as the out-group (although there are frequently multiple out ), inappropriate jokes, sketches and drawings, writings and other means of expression. The types of books read, websites visited, and social media channels and feeds participated in can also reflect the grievance. Hard looks and other nonverbal body language and hostile demeanor directed toward members of out-group(s) can also indicate a grievance. The person holding a grievance may also attempt to recruit other people they perceive to be members of their “in-group” to embrace their ideology. These recruitment attempts can be either overt or subtle depending on the person and grievance narrative.
In cases involving unstable individuals, grievances can sometimes be seemingly irrational or unreasonable. For example, a belief that another person or organization is controlling the aggrieved person’s mind, or that the person is the “real partner or spouse” of a celebrity.
The second step in the pathway to violence is violent ideation, in which the person holding a grievance begins to harbor thoughts or fantasies of hurting or killing the person they have a grievance against, or members of the out-group(s). For example, as mentioned above, a jihadist may hold the belief that Islam is under attack. This is a grievance. When jihadists begin to think about hurting or killing those they hold responsible for attacking Islam, such as the artists who drew inflammatory cartoons of the Prophet Mohammed, he has moved on to the ideation phase. Sometimes this ideation starts indirectly, e.g., “someone should kill them all,” and then later progresses to “I should kill them all.” It is not unusual for a potential attacker to share these thoughts, fantasies and attitudes with friends, colleagues or in online forums. When a person shares violent ideation that may signal an impending violent act, it is called “leakage.” Such leakage can occur in many forms, including conversations, utterances, threats, letters, emails, voice mails, manifestos, diaries, videos, etc.
I’d like to pause here to point out that like the attack cycle, the pathway to violence model must be considered an elastic rather than rigid guide. People move along the pathway at different paces, and in fact, most people do not progress through all the steps and conduct an attack. Many people with grievances never progress to violent ideation, and not everyone who fantasizes about conducting a violent act progresses to planning and preparing for one. Furthermore, the pathway is not a one-way street. Not everyone who begins to plan an attack follows through by executing the plan. People can deescalate, either through outside intervention or due to internal factors.
Once a potential attacker goes beyond mere ideation and decides to act, the pathway to violence then begins to intersect with the activities and behaviors associated with the attack cycle, to include target identification and selection, planning and preparation (training, weapons acquisition, etc.), and finally, deployment and attack. During these three phases of planning and research, preparation and probing and breaching, those planning an attack are vulnerable to detection by the target.
While the pathway to violence model is most often associated with workplace violence, intimate partner violence, and school shootings, it also clearly applies to terrorist suspects. Governments have become increasingly competent at identifying and establishing contact with people in the earlier stages of the pathway to violence before they can get into contact with real terrorist facilitators. Because of this, the criminal complaints and indictments filed in connection with government sting operations targeting jihadists, anarchists and white supremacists provide a very clear view into the grievances and violent ideation of these suspects. Parents, community members, religious leaders and others have also come to understand the importance of spotting and reporting people holding grievances or who have begun to fantasize about conducting an attack. This realization is one of the big reasons the “see something, say something” approach has been successful in thwarting so many attacks.
Investigations into terrorist attacks also frequently provided ample evidence of grievances and violent ideation. But in most terrorist cases, the victim doesn’t have visibility into the grievances and ideation driving the attacker. Because of this, the victim’s first chance to detect attack related activity is when the planning phase of the pathway to violence begins – which is roughly analogous to the attack cycle.
In most cases, the victim or target of an attack will only be aware of the assailant’s grievance and violent ideation if they have contact with them. This contact can be in person or by letter, email, etc. The pathway to violence model is thus widely used for assessing threats related to workplace violence, stalkers, school shooters, etc. Monitoring these contacts or communications can help provide a way to assess where the subject is on the pathway to violence and progress along the pathway can serve as tripwires for action. People holding onto grievances must be taken seriously and carefully assessed and investigated to determine if they pose a potential threat. If possible, their communications should also be kept for later reference. If deemed necessary, strategies to protect the potential target or otherwise mitigate the threat should be developed and implemented.
As noted above, not every person with a grievance or who even begins to have violent ideation will become an attacker. Nevertheless, it is important to train the entire workforce about these concepts, and then establish a mechanism for reporting employees with deeply held extremist or other grievances, or who have exhibited leakage of violent ideation or that they are planning an attack.
This bring us back to the importance of protective intelligence teams. Protective intelligence teams play a critical role in helping companies stay “Left of Bang” by providing training to the workforce and other members of the security teams, assessing and investigating potential threats, watching for potential surveillance, or signs that the potential threat actor is progressing along the pathway to violence.
