Anatomy of a Foiled Plot
By TorchStone VP, Scott Stewart
Image Source: Turtle Island Liberation Front Instagram Post from October 21, 2025.
On December 15, 2025, Attorney General Pam Bondi announced in a post to her X account that the U.S. Government had prevented a “massive and horrific terror plot in the Central District of California.” The plot was thwarted by the arrest of four people who were allegedly connected to the “Turtle Island Liberation Front,” a group the Attorney General characterized as a “far-left, pro-Palestine, anti-government, and anti-capitalist.”
According to a criminal complaint filed in the case, the four suspects were reportedly arrested while they were testing explosive devices in the California desert in preparation for attacks against two unidentified companies at midnight on New Year’s Eve. The U.S. Attorney’s Office in Los Angeles indicated the group was targeting “logistics centers.”
The sensational claims about the Turtle Island Liberation Front and its bomb plot grabbed headlines and attention, but an examination of the complaint reveals that, like the would-be terrorist suspects in many recent thwarted plots, the suspects in this case were far more aspirational than operational—but that does not mean that they did not pose a threat.
The Group
The “Turtle Island Liberation Front” is an anarchist affinity group that emerged from pro-Palestinian, anti-Israel, anti-capitalist, and anti-government activists in the Los Angeles area. These activists have held protests weekly at various sites in Los Angeles since the deadly October 7, 2023, Hamas attack against Israel and throughout the war that followed. Many of these same activists have also turned their attention to protesting Immigration and Customs Enforcement (ICE) activities in Los Angeles. Some of these protests have turned violent.
As is common in many protest movements, there are elements among these Los Angeles activists who called for peaceful protests, while more radical elements argued that violence was needed to achieve their goals. It appears that some of these more radical elements found each other and formed an affinity group they called the Turtle Island Liberation Front. The affinity group launched an Instagram account in July 2025, and the group was composed of anarchists, as can be ascertained by their radical rhetoric, calls for direct action violence, choice of colors, and requests for participants in their protests to wear black bloc attire. Due to the radical and incendiary nature of their posts, some other activists even accused the group of being government provocateurs.
The group quickly came to the attention of law enforcement by posting items on their public Instagram accounts, such as “Death to America,” and “Peaceful Protest Will Never Be Enough,” among other calls to violent revolution.
The Investigation
Given the group’s violent rhetoric, it is not surprising that the FBI deployed a paid confidential informant (confidential human source or “CHS” in FBI parlance) to infiltrate the group to determine if they posed an actual threat. According to the criminal complaint, the Turtle Island Liberation Front affinity group had two levels. The more radical members of the group communicated via a restricted chat group on the Signal messaging application that they christened with the melodramatic name “Order of the Black Lotus.” The criminal complaint reports that one of the female suspects, Audrey Carroll, operated the group’s Instagram account and was also the driving force behind the attack plan.
We know from the criminal complaint that by late November, the CHS had been able to gain the trust of the more radical core group to the point that they were admitted to the “Order of the Black Lotus” chat group and invited to participate in the bombing attack. The complaint notes that during an in-person meeting on November 26, the CHS was provided with a handwritten copy of an operational plan for the attack that Carroll had named “Operation Midnight Sun.” The plan called for five backpacks containing what Carroll termed “complex” pipe bombs to be placed at designated locations belonging to two unidentified U.S. companies. Later in the complaint, the “complex” pipe bomb devices were described as rudimentary pipe bombs taped together.
The plan called for a group of four activists on the ground and one support person who was not on site. According to the complaint, during a December 7 meeting, another suspect agreed to help conduct the attack, along with an undercover FBI employee, giving the group enough people to execute the plan. Three of the four on-the-ground attackers were to place backpacks at assigned locations at the targeted buildings, and the fourth was to paint a red triangle graffiti symbol on the sidewalk to tag the attack.
An inverted red triangle is a symbol derived from the Nazi concentration camp patch placed on political prisoners and has been widely adopted by anti-fascist activists for many decades. Since October 2023, it has also been adopted by pro-Palestinian activists, in homage to the red triangle contained in the Palestinian flag.
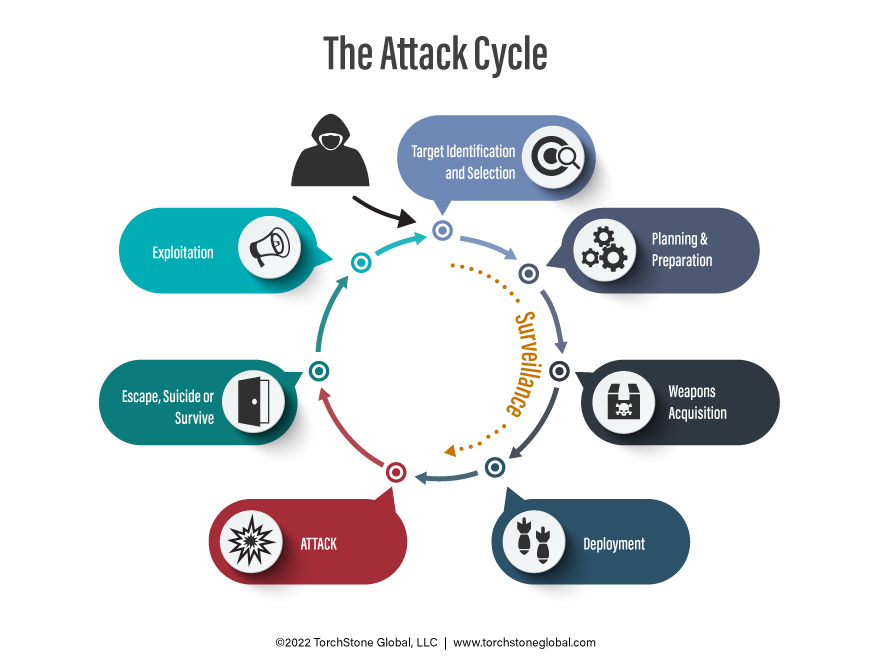
With the targets selected and identified, and attack assignments made, the group then discussed how they were going to conduct preoperational surveillance of the targeted buildings. They also agreed to begin the weapons acquisition phase of their attack cycle.
Using their encrypted “Black Lotus” Signal group, the members discussed the components needed to construct the pipe bombs and the homemade low-explosive filler that would serve as the main explosive charges placed in the pipes. The group then began to collect the items needed to manufacture the pipe bombs with the intent of meeting at a location in the California desert to construct and test the devices on December 12. It was at this meeting in the desert that the trap sprang, and the group was arrested as they began the process of creating the homemade gunpowder they planned to use to fill their pipe bombs. The FBI subsequently arrested a fifth person in Louisiana with suspected ties to the same group, accused of plotting an attack against ICE in New Orleans.
Key Takeaways
First, it is very apparent that Carroll and the other co-conspirators were far more aspirational than operational. Their operational security was lax, and the FBI CHS was in on the bombing plot almost from its inception due to their previous, very public demonstrations of violent intent.
They knew that operational security was needed, and they discussed several security measures such as leaving their own electronic devices at home and only using burner phones during the operation, the need to not leave DNA evidence on the devices or at the attack site, the need to change clothing to throw off pursuit after the attack, and even discussing placing a pebble in their shoe to alter their gait. But fortunately, they were negligent in critical security measures such as vetting the people they admitted into their plot.
Their bomb making tradecraft was also extremely rudimentary, and they had very little idea of how to construct a pipe bomb. For example, they brought sections of PVC pipe out to their desert testing site, but nobody thought about the need to have end caps to seal the pipes and cause them to explode rather than allowing the gases from the gunpowder to just vent out the open ends. Their decision to attempt to manufacture homemade gunpowder rather than use readily available low-explosive mixtures likewise demonstrates their amateurishness.
Amateurs Can Be Deadly
At the present time, Russian intelligence officers are conducting a hybrid warfare campaign that uses social media to recruit people to conduct attacks in Ukraine and NATO countries. Given the ideology of the members of the Turtle Island Liberation Front, they were ripe for recruitment by a power opposed to the U.S. government. Had a Russian intelligence officer succeeded in recruiting the members of this cell before the FBI’s CHS reached them, this plot could have ended quite differently. Working under the direction of an expert, even blundering, amateurish operatives can pose a significant threat. Richard Reid, the bumbling al-Qaeda operative who attempted and failed to detonate a shoe bomb aboard a loaded passenger aircraft in December 2001, serves as a prime example of the threat posed by “Kramer” terrorists who are equipped and directed by trained professionals.
According to the complaint, group members also discussed obtaining firearms (presumably from their co-conspirator in Louisiana) and attending firearms training courses. They further discussed conducting follow-on bombing attacks against additional targets, such as ICE vehicles. Had the group not been infiltrated and had it succeeded in carrying out the New Year’s Eve attack, it is quite possible that, even without expert guidance, members could have applied lessons learned to improve subsequent attacks.
History provides several historical examples of self-taught bombmakers who learned from early mistakes and became more effective over time, including Ted Kaczynski and the Weather Underground. It is also important to remember that even untrained individuals can pose very real threats, as illustrated in the July 2024 attack against President Trump in Butler, Pennsylvania, and the September 2025 murder of Charlie Kirk in Utah.
Low-explosive-filled pipe-bomb-type devices are also nothing to sneer at. As demonstrated by the 2014 Boston Marathon bombing, if properly constructed and employed, they can be deadly.
These points underscore the reality that it is unrealistic to expect the FBI to identify and infiltrate every cell planning and attack or thwart every plot by a lone actor. Given the sheer number of potential threat actors in circulation, doing so is simply impossible.
This reality makes it incumbent upon companies and organizations to take ownership of their own security. All threat actors must progress through the attack cycle to conduct a targeted attack. They are constrained by the demands of the attack cycle and are vulnerable to detection as they progress through the steps required to conduct an attack. Spotting the preoperational surveillance being conducted on a potential target remains one of the best ways to disrupt and prevent an attack.