Cyber Threats Part 2: Phishing and Spear Phishing Attacks
By TorchStone Senior Analyst, Ben West
Phishing attacks, and more specifically, targeted spear phishing attacks, are one of the most common types of reported cybercriminal activity in the United States.
According to the FBI’s Internet Crime Complaint Center, phishing attacks made up just over 38% of 847,376 reported cyberattacks in 2021.
Phishing attacks use social engineering to convince an individual to open a file or click on a link that infects their electronic device with malware and allows the attacker some level of unwanted access to a user’s accounts, devices, or even the entire network.
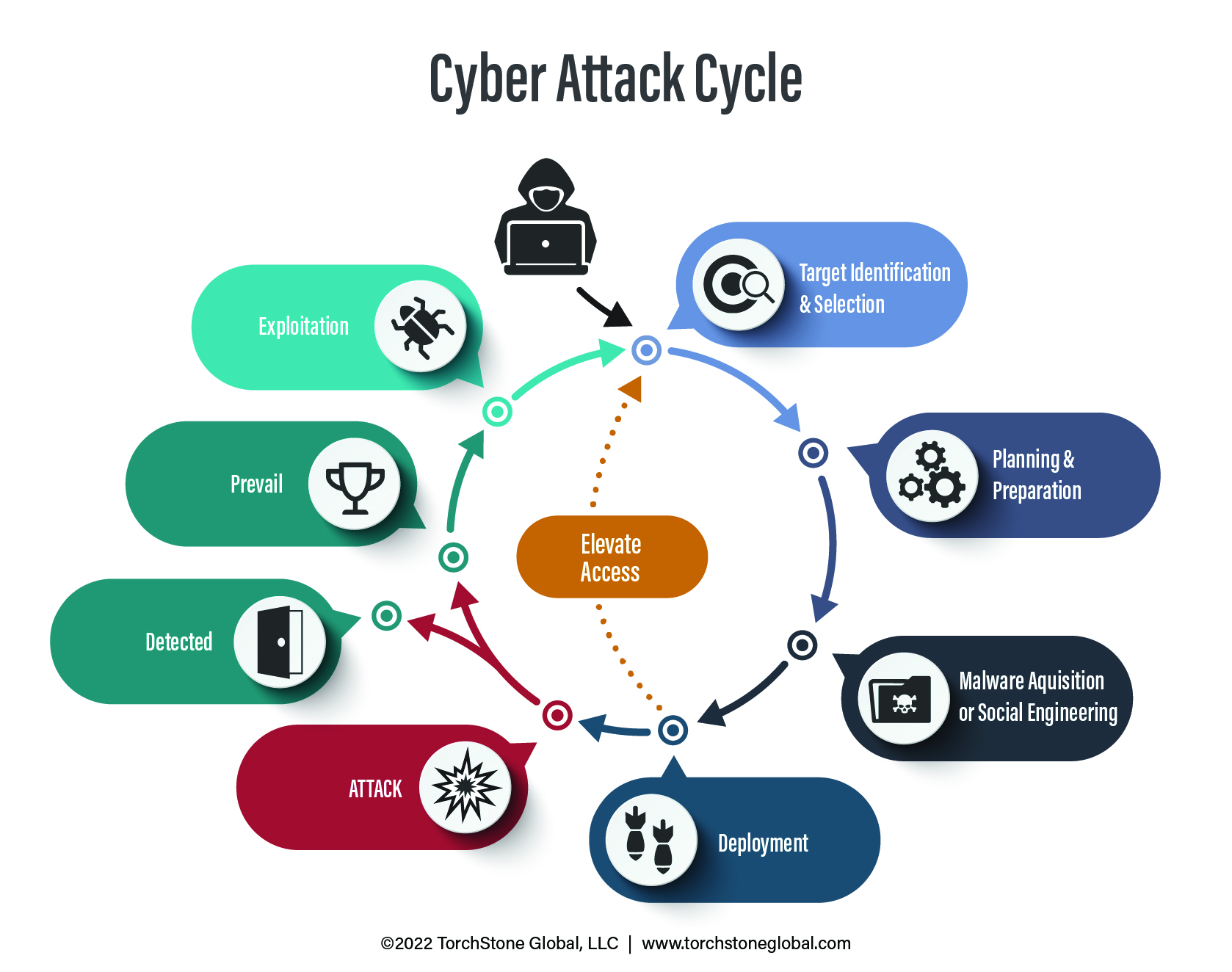
In the Cyber Attack Cycle, attackers typically use phishing attacks to establish a foothold within their victim’s device or network in order to conduct more surveillance and collect more information in order to launch a more sophisticated (and lucrative or disruptive) attack later on.
Dangling the Worm
Generic phishing attacks are typically easy to spot and easy to avoid.
They look like spam, promise results that are clearly too good to be true (e.g., unexpected inheritance windfalls or promises of sexual performance improvements) and anyone with basic experience using emails or text messages knows to either ignore them or better yet, to delete and report them to their IT department as junk or malicious.
But as internet users grow savvier, attacks have grown more sophisticated.
Modern-day phishing attacks can exploit current events, imitate legitimate websites, and exploit internet users’ security concerns to trick them into providing personal information.
Setting the Hook
For example, modern phishing campaigns may include fake, but realistic-sounding news headlines goading the recipient to click on the link to learn more.
They may take advantage of current events such as the war in Ukraine by using subject lines such as “Russia Withdraws Military Forces From Ukraine” to lure recipients into clicking what appears to be a link to the news story.
But the link may actually take the user to a corrupted website that loads malware to their computers.
Other tactics exploit more mundane day-to-day email tasks by, for example, mimicking an email from Dropbox to alert a user that they have received files and need to log in to their account to access them.
The link may take the victim to a site that looks identical to their Dropbox login page, but it is in fact an imitation.
When the user enters his or her login credentials, they are logged by the attacker who can use them to extract more information later.
Email attachments claiming to be bank statements, invoices, or resumes from prospective employees are also popular ways to convince victims to open files that infect their device with malware and grant the attacker access.
Reeling in the Big One
The difference between phishing and spear phishing is the degree of specificity.
Phishing attacks are generally not specific to the user and sent out to tens of thousands of email accounts at a time.
Spear phishing, on the other hand, is typically more targeted and tailored to a specific victim than a generic phishing attack—spear phishing prefers quality over quantity.
If an attacker has identified a vulnerable target and collected a few datapoints (such as family member names, employer, hobbies, etc.) they can craft a more believable message to the victim that may appear to come from their parent, co-worker, or promote a sporting event that the potential victim has demonstrated interest in.
The more intelligence the attacker has on the victim, the more detailed and believable the approach may be.
If, for example, the attacker knows that the victim has an upcoming flight to New York on American Airlines, they can craft an email imitating the airline with fake links encouraging the victim to log in to their account to check updated flight information.
Or they may disguise malware in a PDF claiming to contain boarding passes for the flight.
My Voice is My Passport
Even the most sophisticated spear phishing attacks are vulnerable to detection and wary users can avoid becoming a victim.
Most malware in circulation that phishers and spear phishers rely upon to infect and gain access to their victim’s devices rely on bugs and exploits that are already known.
Keeping software patched and up to date will prevent an attack from being successful even if the user clicks a bad link or opens a corrupted file.
However, since it is difficult to know specifically what type of malware is lurking behind a suspicious email, the user should never assume they are protected and always avoid exposing their devices to malware.
Tell-tale clues of a phishing or spear phishing attack include sender email addresses with misspellings or alternate suffixes, links to websites that do not appear to be the one advertised or appeals to urgently complete a requested task.
The sender’s email address may appear similar to the actual address, but may include a typo, or use “.net” (or other URL suffixes) instead of “.com.”
The user can hover their cursor over the link to preview the URL it will take them to and determine if it appears to be safe or not, being aware that spear phishers may also imitate legitimate websites with slight misspellings or alternate suffixes.
Like other scammers, spear phishing attacks also appeal to urgency, warning the victim that they are at risk if they do not click on a link or view a document immediately.
This is an effort to rush the potential victim into a rash decision rather than more carefully checking the clues outline above.
Verify Me
When in doubt, it is best to verify an email or text message through alternate means.
Rather than clicking the link purportedly from Dropbox or American Airlines or any other service you may have an account with, open a new tab in your browser and log in to your account to confirm whether there really is a new document to view or updates to your upcoming flight.
This puts control over accounts back in the hands of the user and avoids relying on email or text messages, which can easily be used for nefarious purposes.
Finally, if you suspect that you have been victimized by a phishing or spear phishing attack, report the matter immediately to your IT department.
As mentioned in the beginning, phishing attacks are often used to establish a foothold on a device or network to collect more intelligence so that the attacker can elevate access and cause more harm in the future.
The faster a phishing attack is caught and addressed, the lower the likelihood that the attacker can exploit the access and cause more damage in the future.
This report is the second in a five-part series addressing cyber threats to organizations and individuals. The first part of the series, Understanding the Cyber Attack Cycle, introduces the Cyber Attack Cycle and its progression. The third part, Business Email Compromise, illustrates how information received from a spear phishing attack may be used. The fourth part, Ransomware Attacks, discusses how information or network access may be held hostage. The fifth and final part of the series, Supply Chain Attacks, contends with the failure to secure a network.