
Cyber Threats Part 4: Ransomware Attacks
By TorchStone Senior Analyst, Ben West
On May 5, 2022, AGCO, a manufacturer of agricultural equipment, was targeted in a ransomware attack that disrupted production and distribution of equipment at several of its facilities.
Over the following week, the company’s stock price fell 13% as executives rolled out their response to the attack.
The company was able to resume operations at its plants within about two weeks of the attack and assured the public that it would make up for lost production later in the year.
However, the timing of the attack–during the spring planting season—jeopardized the availability of equipment and parts to support farmers during the crucial time.
Less than two weeks before the ransomware attack, the FBI had warned that cybercriminals would be targeting the agricultural sector during the sensitive time: they had already targeted several granaries during the harvest season of 2021.
Access Prohibited
Ransomware attacks like the one that targeted AGCO take information or networks hostage and only release control once an agreed-upon sum has been paid—similar to the mechanics behind a kidnapping for ransom criminal operation.
However, ransomware attacks can be launched anonymously, without any physical interaction between the criminals and victims.
The criminals infiltrate the ransomware code into the target’s electronic device or network (often through phishing tactics) and take control of vital databases, programs, networks, or system controls.
The criminal actor then negotiates a sum (“ransom”) to be paid in exchange for relinquishing control of the seized asset and allowing systems to return to normal.
In the AGCO case (and most cases of ransomware) it is not clear if the company paid or did not pay, but over 75% of all organizations hit by attacks end up paying some amount of ransom.
In 2021, the average ransom payment reached $812,000, according to Sophos’ Ransomware 2022 Report.
However, ransom payments vary by industry, with more time-sensitive manufacturing companies and energy utilities paying an average of $2 million per attack.
Local governments and the healthcare industry are more often targeted, but their tighter budgets yield lower ransoms, averaging around $200,000 each in 2021.
Rock and a Hard Place
Like phishing and Business Email Compromise attacks, the effectiveness of ransomware attacks is just as determined by timing and intelligence as the malware used.
Ransomware packages are available to anyone who wants to purchase them on dark web marketplaces, but successful ransomware attacks are more specifically timed and targeted.
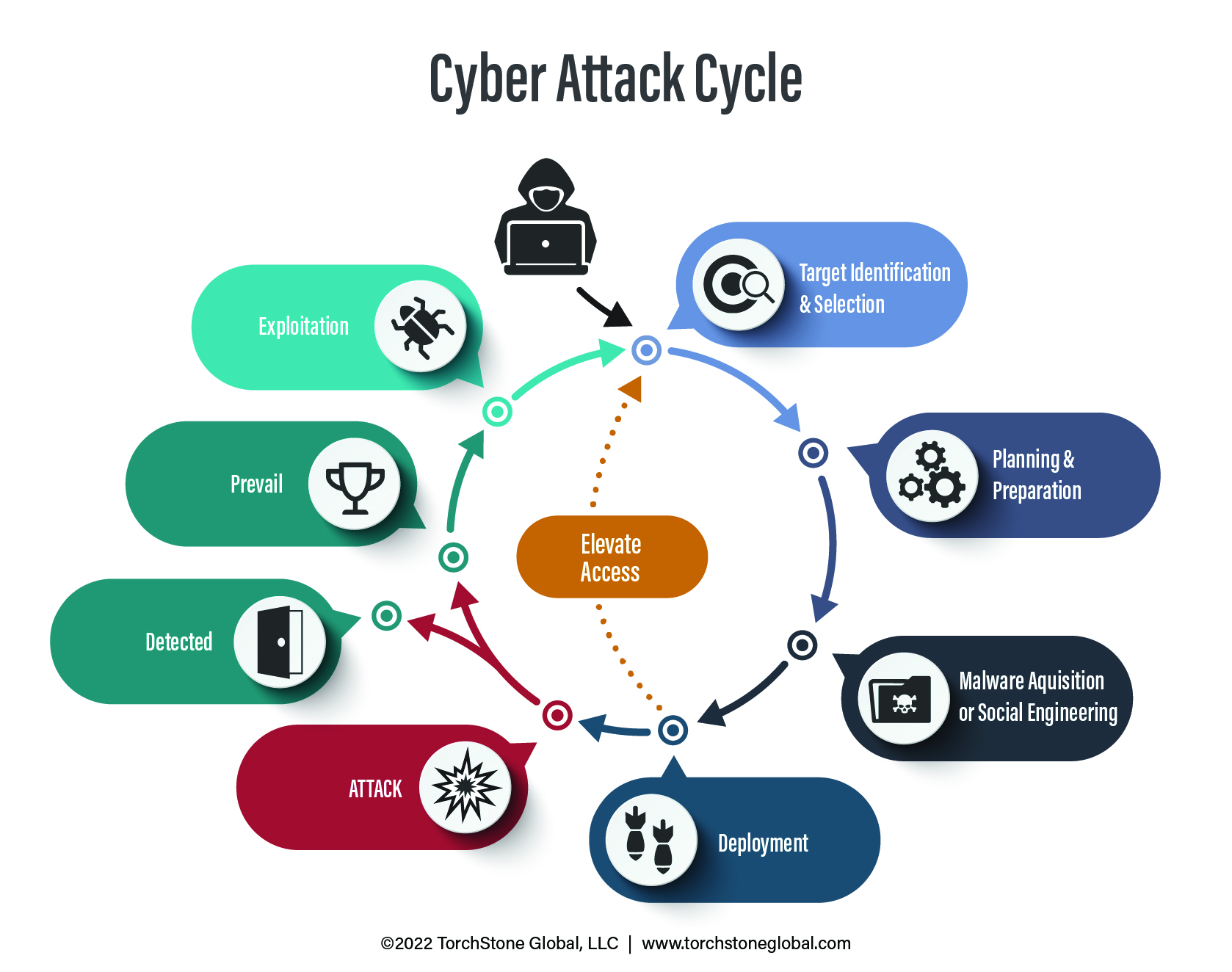
With AGCO, the attackers struck during one of the most crucial times of the year for the company.
This maximized pressure on company executives to convince them to pay up and regain functionality rather than lose precious time (and customers) trying to repair the issue themselves.
AGCO is by no means alone when it comes to ransomware attacks disrupting industrial processes and the markets they serve:
- In February, 2022, the world’s largest carmaker, Toyota, announced that it had to suspend operations on all its production lines in Japan for 24 hours due to a ransomware attack that compromised a parts supplier.
- In May 2022, Russian ransomware gangs Hive and Conti compromised dozens of Costa Rican government offices, right as President Rodrigo Chaves Robles was assuming office. One of his first acts as President was to declare a State of Emergency in the country due to disruptions to government offices caused by the attack. President Robles has claimed that the attacks were facilitated by his political rivals to undermine his administration.
- In May 2021, the Russian-based REvil ransomware group sent fuel prices surging along the east coast of the United States after causing the Colonial Pipeline to shut down due to a ransomware attack. That attack was one of the few to attract support from the Russian government, which later arrested members of REvil ransomware group and claimed to have disrupted their operations.
However, Russian authorities typically ignore cybercriminal groups operating on their territory—as long as those groups focus their efforts on European and North American targets and cooperate with Russian authorities when needed.
And while most Ransomware attacks aim to be disruptive to extract payments from their victims, sometimes disruptive, punitive attacks (potentially state-backed) can come in the form of Ransomware attacks.
For example, the 2017 NotPetya attack linked to Russia caused hundreds of millions of dollars in damages to major global companies such as shipping giant, Maersk, without seriously attempting to extract ransoms from the victims.
Guarantees Not Given
In countries like Russia, where the state has a history of working with criminal groups, the line between financially and politically motivated attacks is blurred.
The blurred line between financially and politically motivated attacks makes it difficult to assess whether to pay ransom after being attacked.
Paying a ransom does not necessarily guarantee a resolution of the attack, either because the attack is meant to be as disruptive as possible (with no regard for profit) or because many ransomware attackers are only concerned with collecting payment and not on fulfilling their promise to restore systems.
Despite the high rate of ransom payments reported in 2021, the FBI and most western law enforcement agencies discourage victims from paying ransoms because doing so encourages further attacks and provides revenue to criminal organizations to grow more potent.
For these reasons, the ideal response in a ransomware attack is to abandon the data compromised in the attack and revert to backups stored on separate networks.
Since the exact timing of a ransomware attack is impossible to predict, this means that organizations should keep updated backups of their systems in order to minimize disruptions caused by ransomware attacks.
The other crucial element of avoiding ransomware attacks is awareness by staff to avoid suspicious emails and document attachments that could infect electronic systems and to report suspicious network activity immediately to mitigate the impact of breaches.
This report is the fourth in a five-part series addressing cyber threats to organizations and individuals. The first part, Understanding the Cyber Attack Cycle, introduces the Cyber Attack Cycle and its progression. The second part, Phishing and Spear Phishing Attacks, demystifies the most common cyber security threat. The third part, Business Email Compromise, illustrates how information received from a spear phishing attack may be used. The fifth and final part of the series, Supply Chain Attacks, contends with the failure to secure a network.
