
Cyber Threats Part 1: Understanding the Cyber Attack Cycle
By TorchStone Senior Analyst, Ben West
Cyber attacks leverage information to gain access to proprietary networks, electronic devices, and chains of command in order to gain intelligence, funds, cause disruptions, or all of the above.
Attackers can range from the highly sophisticated, state-backed advanced persistent threats to well-organized, financially motivated criminal groups, to more rudimentary individual scammers.
Per the FBI’s Internet Crime Report 2021, cyber attacks and associated financial losses have been steadily increasing over the course of the 21st century and have become a routine area of concern for corporate security professionals.
The COVID-19 pandemic only exacerbated the rate of attacks and financial losses as employees worked on more vulnerable home networks. Criminals exploited the confusion of the pandemic to take advantage of more victims.
Even as the pandemic recedes and employees return to offices, there are no indications that the rate of cyber attacks will decrease anytime soon.
Fortunately, major losses associated with cyber attacks are preventable and understanding how these attacks work is a major component of prevention.
The following five-part series will explore the Cyber Attack Cycle and how it applies to malware and social engineering use in several common types of cyber attacks, including phishing, business email compromise, ransomware, and supply chain attacks.
The Cyber Attack Cycle
Companies that understand the full cycle of a cyber attack are in a better position to avoid or prevent them. Such attacks can be multiple, in tandem, and assorted.
However, they also follow a similar process to a physical attack cycle—a cycle that can be detected and interrupted.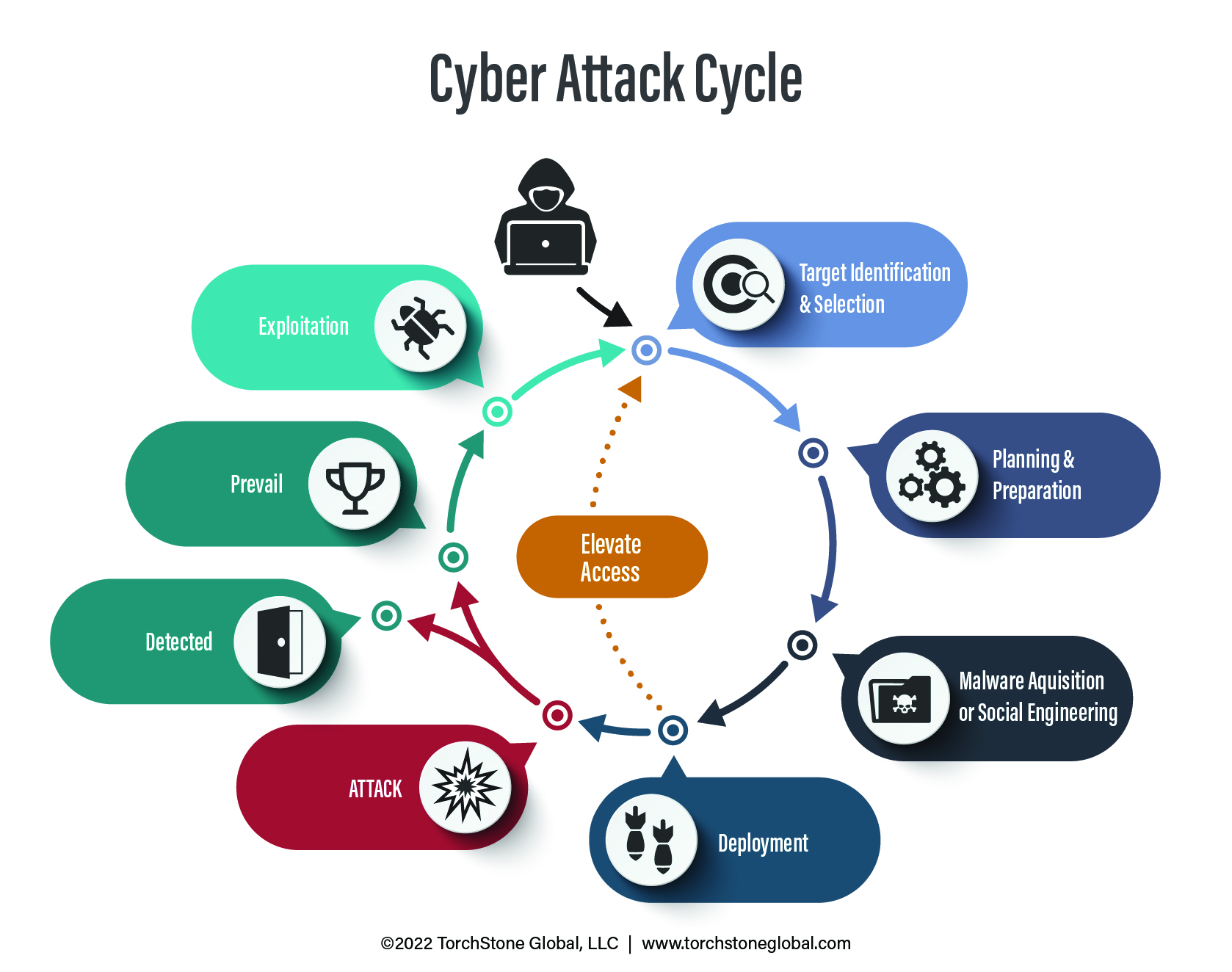
The cycle begins with intelligence gathering.
It might start as innocuously as searching for employee contact information on social media platforms such as LinkedIn or sketching out corporate structures through open-source reporting (publicly available information).
The attacker can leverage information about the victim (such as the names of relatives, business associates, or other familiar names) to increase the likelihood that the victim complies with requests that allow the attack to be successful.
After identifying a target and a few generic details about their responsibilities and social network, the attacker may prepare an attack by purchasing malware online.
Phishing kits, ransomware packages, and other tools valuable to cyber criminals are widely available online and cost anywhere from a few bucks to thousands of dollars depending on their sophistication.
After acquiring the malware (i.e., the “weapon”) the attack on the target can commence.
In the deployment phase, the attacker may also further his informational advantage and elevate access even more by targeting others in the hopes of gaining more valuable intelligence, funds, or causing larger disruptions.
If the attack is successful and the attacker is able to collect sensitive credentials or gain access to a proprietary network, the attacker can continue to exploit his access for further criminal gains.
Should the attack be detected, it does not eliminate the possibility that other cyber attack cycles are already occurring.
Identifying the Threat
The following series will explore how cyber attacks work by studying four popular tactics: phishing, ransomware, business email compromise, and supply chain attacks.
Each tactic can be used by itself or in combination with others.
Given the proliferation of off-the-shelf malware available online, none of the tactics require advanced computer skills. However, coding and programming skills certainly help enhance the potency and damage caused by an attack.
Cyber attacks target accounting departments, sales, research & development, and the executive C-suite, so a well-defended company must rely on the wherewithal of all its employees to identify and avoid would-be cyber attacks.
Just like physical attacks are most susceptible to disruption during the pre-operational phase, cyber attacks can also be mitigated by identifying intruders as early as possible and denying them from maintaining access to proprietary networks to prepare for larger attacks.
Typically, the more sophisticated the attack, the more planning, intelligence gathering, and access are required. This means a longer pre-operational phase and therefore more opportunities for detection and prevention.
Responding to the Threat
However, cyber security is not just the responsibility of the information and/or physical security department.
While a general return to offices behind the defenses of better-protected networks will help reduce the vulnerability of employees to cyber attacks, it is clear that the threat is here to stay.
Work from home arrangements necessitated by the COVID-19 pandemic accelerated existing cyber crime growth trends and each of the tactics mentioned is growing in frequency and causing larger financial losses every year.
Virtually every company has already been targeted by these tactics and many have become victims.
While it is still certainly important to invest in cyber defenses and training to avoid these attacks, companies also need to accept the fact that falling victim to these attacks is inevitable.
Robust response strategies are a necessity to identify and stop breaches and mitigate the damage they cause.
This report is the first in a five-part series addressing cyber threats to organizations and individuals. The second part, Phishing and Spear Phishing Attacks, demystifies the most common cyber security threat. The third part, Business Email Compromise, illustrates how information received from a spear phishing attack may be used. The fourth part, Ransomware Attacks, discusses how information or network access may be held hostage. The fifth and final part of the series, Supply Chain Attacks, contends with the failure to secure a network.
