Lessons from a Thwarted Plot in Michigan
By TorchStone VP, Scott Stewart
Thirteen people have been arrested in connection with a large, multi-state investigation into domestic terrorist activities. Six of them were charged by federal officials with plotting to kidnap Michigan Governor Gretchen Whitmer, while the remaining seven face state charges for allegedly attempting to identify the homes of law enforcement officers to launch attacks against them.
A review of the criminal complaint filed in the federal case contains a number of important lessons for security professionals.
The Importance of Grassroots Defenders
The first is the importance of what I call “grassroots defenders.” Grassroots defenders are ordinary citizens or police officers on patrol who notice and report suspicious behavior. Despite their global mandate, the FBI is a relatively small agency and cannot monitor everything all the time. The FBI has a little over 13,500 special agents to carry out the array of global programs they are charged with. Counterintelligence, corruption, white collar crime, and other investigations all compete with the counterterrorism mission for the Bureau’s personnel and other resources. The FBI thus relies heavily on reports of suspicious behavior from concerned citizens and police agencies. Some people have mocked the simplicity of the “see something say something” mantra, but it works, as it did again in this case.
The FBI became aware of the individuals involved in this case when a concerned individual reported to the police that a militia group was attempting to identify the residences of police officers so they could target them for attacks. An investigation was initiated and showed that these people were involved in a militia group that called itself the “Wolverine Watchmen.” It appears that at least one of the members of the militia disagreed with the plan and alerted the police. FBI agents interviewed members of the militia group about the police plot and convinced at least one of them to become a confidential informant. The FBI was able to eventually recruit at least two informants within the group (the complaint suggests there were more). They also were able to place two undercover agents into the plot. But without the initial report from the disaffected militia member, the FBI may not have gotten wind of the group.
Law enforcement and security professionals should continue to educate the public about the importance of reporting suspicious behavior and indications that a person or group is progressing along the “pathway to violence.”
Pathway to Violence
The complaint provides a good chronicle of the group members’ pathway to violence, as they progressed from a grievance, through violent ideation, and ultimately toward planning an actual attack.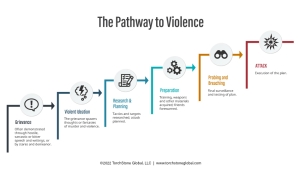
In this case the group’s grievance narrative was that they believed Michigan Governor Whitmer was being oppressive in the way she was handling the COVID-19 crisis, and that the closures she ordered were hurting business owners and workers. Michigan saw a wave of protests in the Spring over the lockdown, including a highly publicized one on April 30, in which scores of protesters, some of them armed, stormed Michigan’s capitol building.
It appears that these protests were the catalyst for first the violent ideation of targeting police and later for the plot to kidnap the governor. Indeed, it was that violent ideation of targeting police that alarmed the first informant, causing him to contact police. The cell was subsequently thoroughly infiltrated before they progressed to researching and planning, much less preparing for, the attack against the governor.
This chain of events also suggests that the most violent fringe of the militia movement remains fairly small and marginalized; and that while some members of the movement may be willing to train and prepare for self-defense, they do not approve of offensive violence targeting innocents. This is a divide that law enforcement can continue to exploit.
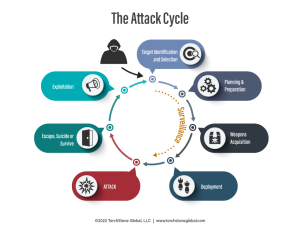
The Attack Cycle
The affidavit in this case also provides a good overview of the militia’s attack cycle – they identified their target, began to plan and prepare for the attack, discussed acquiring explosives, and then conducted surveillance of the governor’s vacation residence.
According to the description of the surveillance on the governor’s residence, it appears to have been unprofessionally conducted, with little in the way of cover for status or action. In other words, the group of men inside the car driving slowly through the neighborhood and taking photos and video of the house had no plausible reason to be there doing what they were doing. Surveillance is an unnatural behavior, and it takes time and training to master the art. Very few criminals and terrorists have put in the effort to develop good surveillance tradecraft, resulting in shoddy surveillance that has long been one of shortcomings of terrorist plotters.
While many portions of the attack cycle can be conducted secretly and out of sight of the potential target, during surveillance, would-be attackers are forced to reveal themselves. This makes surveillance one of the largest vulnerabilities of the attack cycle, especially if the target has well-trained protective agents who are looking for surveillance. In this case, had the authorities not been aware of this group before they began conducting surveillance on the residence, they likely would have picked up on them at this juncture of the attack cycle because of their sloppy tradecraft.
Lack of Terrorist Tradecraft
Surveillance was not the only element of terrorist tradecraft this group struggled with. The complaint outlined the group’s struggles to construct even primitive improvised explosive devices using low explosive mixtures such as black powder and commercial fireworks. Their failed experiments with these devices, combined with their desire to blow up a bridge to prevent the police from responding to the kidnapping at the governor’s residence, likely allowed the FBI to insert one of their undercover agents into the plot (similarly, we’ve seen several jihadist, right wing and anarchist plots thwarted when those planning an attack either reached out for help in obtaining explosives, or for someone with bombmaking tradecraft to help them construct a bomb.) In this case, the group agreed to raise $4,000 so that an undercover FBI employee could purchase the explosives they required for their plan.
Speaking of the plan, the group’s operational plan for the kidnapping was also not very well thought. They certainly did not have the type of detailed step-by-step plan that would be associated with a military raid to take down a high value target or a law enforcement plan to execute an arrest warrant on a dangerous individual. This is not surprising given the history of poor planning associated with similar plots. Fortunately, professional terrorist planners like Khalid Sheikh Mohammed or Carlos the Jackal are few and far between, and people who can meticulously plan an attack on their own, like the Oslo Norway bomber/shooter did, are relatively rare.
An element of planning that was particularly poor in this case was operational security. Loose lips do indeed sink ships — or in this case kidnapping plots — and the men spearheading this conspiracy were far too open about their desire and intent to conduct an attack for it to have succeeded. They initially shared critical operational information with too many people, which almost guaranteed that the authorities would learn of their plan. Their search for people to help them gather intelligence and make bombs further jeopardized their security.
Indeed, one of the primary planning and operational security flaws exhibited by this cell was their desire to do something spectacular, rather than something within their means. They had ample men and firearms, and yet rather than use what they had in a simple attack, or even series of simple attacks, they aspired to do something that was beyond their capacity. They had to go outside their group to obtain help from a bomb maker as well as to obtain explosives. This dramatically increased their vulnerability to detection and infiltration.
By holding meetings in a hidden basement beneath one of the suspect’s businesses or in the middle of the woods and confiscating participants’ cell phones, the group’s leaders thought they were being secretive. At this point, however, the plot was already compromised, and the confidential informant who attended the meetings was wearing a sophisticated wire that escaped detection.
The group’s use of social media applications to communicate and their use of simple substitution codes in attempt to fool the authorities were also amateurish, e.g. using the term baker to refer to the undercover FBI agent posing as a bombmaker, and referring to bombs as cupcakes.
Heavy Focus on Domestic Actors
Finally, this case is yet another illustration of the heavy focus law enforcement maintains on domestic terrorist actors, and specifically right-wing extremist groups. It is common to see people accuse the government of ignoring such actors, but when viewed in light of government operations to take down groups such as Atomwaffen, The Base, and sting operations against Boogaloo cells and others, it is quite clear that state, local and federal law enforcement agencies are all keenly aware of the threat posed by right-wing extremist groups, and are using all the tools at their disposal against them. Indeed, many of the tools developed in response to the jihadist threat following the 9/11 attacks have proved to be quite effective against domestic extremists of all stripes.