-

Cyber Threats Part 5: Supply Chain Attacks
The fifth in a five-part cyber threat series focuses on supply chain attacks. This indirect approach will exploit a weakness…
-

Cyber Threats Part 4: Ransomware Attacks
The fourth in a five-part cyber threat series focuses on ransomware attacks where information or computer networks are held hostage…
-
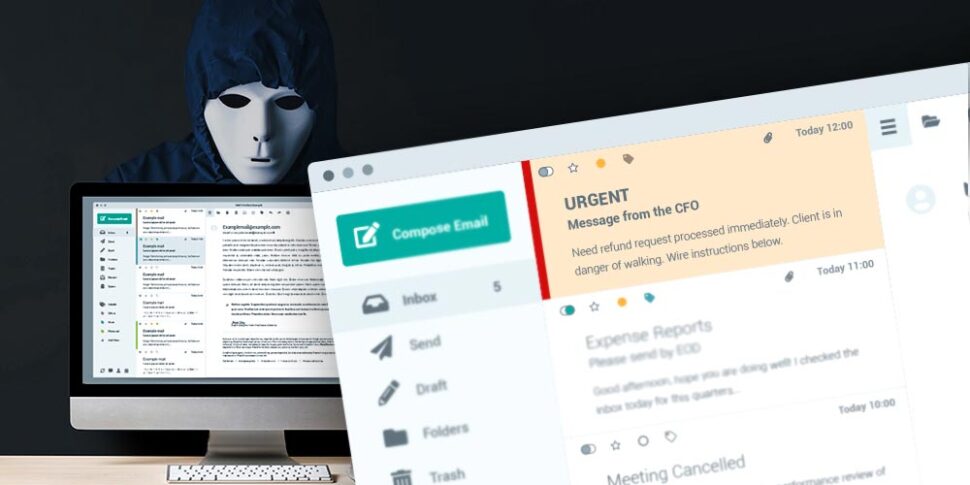
Cyber Threats Part 3: Business Email Compromise
The third in a five-part series demystifies business email compromise schemes and how they target those who transfer funds electronically.…
-

Cyber Threats Part 2: Phishing and Spear Phishing Attacks
The second in a five-part series explores phishing, and the more targeted spear phishing attack, and how they manipulate information…
-

Cyber Threats Part 1: Understanding the Cyber Attack Cycle
Cyber attacks leverage information to gain access to proprietary networks, electronic devices, and chains of command in order to gain…
CALL US: (877) 897-6428
