Threat Comes Home
By TorchStone TorchStone VP, Scott Stewart and Senior Analyst, Ben West
During the many years we’ve spent studying attacks against high-profile individuals, we’ve seen that quite a few notable incidents have occurred at or near their residences. Some of the incidents involving business executives that come readily to mind are:
- The murder of tech CEO Pava LaPere at her apartment in Baltimore in September 2023.
- The murder and dismemberment of entrepreneur Fahim Saleh in his Manhattan apartment in July 2020.
- The kidnapping and murder of tech CEO and cannabis entrepreneur Tushar Atre from his Santa Cruz California home in Oct. 2019.
- The horrific torture and murder of the CEO of American Iron Works and his family at their Washington DC home in May of 2015.
- The murder of retired biotech CEO John Watson at his La Jola CA apartment in June of 2010.
- The kidnapping and murder of Exxon CEO Sidney Reso from his Morris Township New Jersey home in May 1992.
Business executives are not alone in being targeted at their residences. John Lennon was assassinated outside his New York apartment in December 1980, rapper Pop Smoke was murdered during a home invasion robbery at his rented LA residence in February 2020, and hardly a week goes by that we do not hear of a stalker being arrested at the residence of some pop star or famous actor.
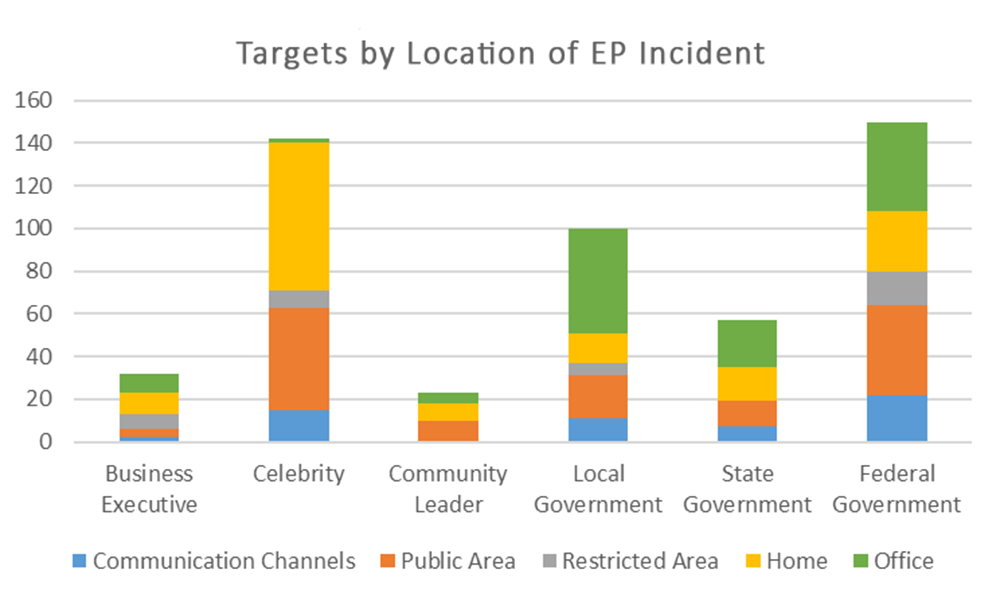
The cases we have tracked as we have compiled our monthly Executive Protection Intelligence reports have also provided data demonstrating how frequently high-profile individuals are targeted at their homes. Of the 504 incidents targeting high-profile individuals we have tracked from April 2023 through May 2024, 29% of them have occurred at or very near the home, making it the most common place where incidents occur. That percentage goes up to 31% for business executives and 49% for celebrities.
Why Residences?
Assailants target high-profile individuals at their residences for largely the same reason law enforcement officers begin their search for criminals at home. It is a known location where the target spends a substantial, and largely predictable, portion of each day.
It is for this reason that the daily home-to-work move has traditionally been considered the most predictable and dangerous time of the day for people being targeted for a terrorist attack or criminal kidnapping.
Secondly, residences tend to have less security than office buildings, meaning that targets are more vulnerable to attack at home than in the office. Also, since most people sleep at their residences, attackers can also take advantage of the darkness of night to help conceal their attack cycle activity.
Activists have also chosen to conduct protests, harassment, and direct actions at the homes of their targets as a way to “personalize” the issue. A CEO may not pay much attention to a protest conducted at a plant, retail location, or even the corporate headquarters, but activists know they will certainly get their target’s attention when they show up outside an executive’s home, place of worship or child’s school.
Mitigation Measures
Perhaps the most important step to keep threats from coming home is to guard carefully the location of the residence. Once an address is posted on the internet, it is very hard to erase it, even with the help of a very effective information removal company such as 360Privacy. It is even more difficult to remove an address if it appears in official government documents such as tax records or filings with the Securities and Exchange Commission and Federal Election Commission.
Because of this, it is important for high profile individuals to buy their residences under an innocuous LLC or other vehicle to disassociate themselves from the property. Transferring it to an LLC after it is purchased is not effective. The LLC should not include the family’s name or be tied to a corporate or other address that would connect it to the principal. Also, if more than one property is owned, a separate LLC should be used for each.
Another common way to identify someone’s residence is through social media posts. Determined individuals with access to social media platforms and Google Maps can correlate seemingly innocuous images of a property to its physical address. In March 2024, police in Madrid, Spain arrested a burglary gang that was targeting soccer players’ homes after identifying them on social media.
Executives should make sure that their own personal accounts and the accounts of others living with them have stringent privacy settings to avoid general public access to their posts. Even then, it’s best to avoid posting images of a home or other sensitive area (like a school) since nothing on the internet is truly private. Based on our experience, social media accounts belonging to children, spouses, and other close relatives of executives tend to have vulnerabilities that criminals or others could easily exploit.
Physically securing a home requires a layered approach involving good coordination with local law enforcement and neighbors, good perimeter security, and, finally, a comprehensive home security alarm system that accounts for all points of entry. Depending on the threat level a principal faces, an occasional police patrol may be necessary. Maintaining good relations with neighbors and sharing information about threats to or irregular activity in the neighborhood is also a good practice for maintaining situational awareness.
While it might sound obvious, ensuring that door and window locks are in good working order and then ensuring that all occupants of the home use them as intended is a commonly overlooked and simple security measure. The final layer of security should be a comprehensive home security alarm system that covers doors and windows—including broken glass panels. Many home burglars have evaded more basic home security systems by breaking in through large glass sheets, such as those found on patio doors.
Finally, conduct periodic drills with your family and household staff. Make sure that they know how to use the alarm systems. No amount of planning and technological security tools in the world can overcome simple human error.