
Kidnapping Part 5: Tiger Kidnapping
By TorchStone VP, Scott Stewart
As the woman opened the door, she was startled by the pair of armed men standing on the porch pointing guns at her.
She quickly slammed the door and ran upstairs.
However, the men used a crowbar to pry open the door and followed her up the stairs where they subdued her and her husband in their bedroom, along with their infant son.
The couple was handcuffed and blindfolded by their assailants.
Although the couple’s home was in a nice neighborhood the armed men were not interested in their possessions.
They were after a bigger score, and the home’s occupants were the key to their scheme.
The pair demanded that the banker go to his place of business and take at least $1 million from the vault.
The banker told the criminals that he was a loan officer and did not have access to the vault, but they replied that they didn’t care.
He was to go to the bank, open the vault, and bring the money to the kidnappers or they would kill his wife and son.
The banker did as instructed and was able to get his branch manager to open the vault for him.
He emptied the vault of its contents, some $195,000, and took the money to the kidnappers who were waiting in his wife’s car with his wife and the baby.
After a short drive to their get-away vehicle, the kidnappers threw the wife’s keys into the woods and abandoned the wife and the baby.
It was a traumatic experience, but at least the banker and his family were able to emerge without being physically harmed.
More Than a Kidnapping
This was not a just home invasion robbery—it was a tiger kidnapping.
Tiger kidnapping is a crime that involves using kidnapping to compel a person to commit a second crime.
For their part, while the tiger kidnappers got away with their loot, they would soon be caught by the FBI in connection with another tiger kidnapping.
Investigators would later find that they had been involved in an interstate crime spree that involved dozens of crimes that included three tiger kidnappings in Tennessee and one in Connecticut.
While tiger kidnappings are often financially-motivated, they can also be used for other purposes.
For example, the Provisional Irish Republican Army widely used tiger kidnappings to compel individuals to participate in terrorist attacks, such as bombings.
Tiger kidnappings have also been portrayed in movies like Bandits, and in books such as Jack Carr’s The Terminal List.
While tiger kidnappings often catch their victims by surprise, like other crimes they do not simply emerge from nowhere.
Tiger kidnappings are the result of a complex planning process that can be detected—and interrupted.
Tiger Kidnapping Attack Cycle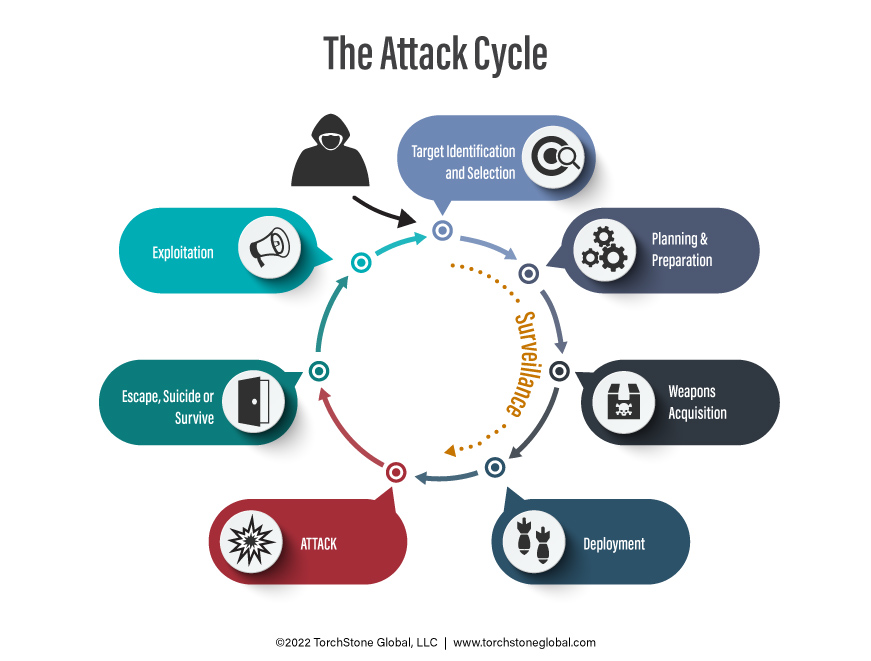
The attack cycle for a tiger kidnapping follows the same general planning cycle used in preparing for any other crime.
However, a tiger kidnapping requires more effort than a traditional bank robbery, a home invasion robbery, or even a kidnapping for ransom, because it involves elements of all three crimes.
In the case cited above, the criminals had to first conduct surveillance on the bank to determine its procedures and to identify their target, who in many cases is the person who opens the vault in the morning.
They then conducted extensive surveillance and relied heavily on bank websites and LinkedIn for their online research to help them select the Vice President who was attacked.
The criminals must then conduct extensive surveillance on the targeted employee to determine their home address and behavioral patterns.
The interstate tiger kidnapping gang used both physical surveillance and hidden cameras to surveil their targets and gain an understanding of their daily routines so that they could pick the ideal time to conduct the home invasion.
Finally, to plan the home invasion and kidnapping portion of the crime, the criminals have to surveil the employee’s residence and determine the best way to enter the residence given the residential security measures in place.
This assessment will also include surveying the neighborhood for potential problems.
Once all this information is gathered, they plan how they will deploy and conduct the home invasion, how they will hold the family member(s), and how they will receive the ransom money and escape.
Preventing Tiger Kidnappings: Potential Victims
The large amount of surveillance required to plan a tiger kidnapping means that the criminals planning it are vulnerable to detection for a longer period than the criminals planning most crimes.
This vulnerability is amplified by the fact that most criminals are simply not very good at conducting surveillance.
Criminals are able to get by practicing terrible surveillance tradecraft—especially bad demeanor—because most victims of tiger kidnappings and other crimes are simply not practicing an appropriate level of situational awareness.
This lack of awareness is often caused by, or in some cases compounded by the wrong mindset.
I have interviewed a large number of crime victims who noticed criminals before they were attacked, but for some reason, they chose not to take action that could have kept them safe.
They either ignored what they were seeing because they did not trust their senses, they were too busy to make the effort to check out the anomaly or to avoid a potential problem, or they mistakenly denied they could or would be targeted.
The three most important steps that individuals can take to avoid becoming victims of a tiger kidnapping:
- Adopting a sound security mindset that recognizes threats do exist
- Accepting responsibility for one’s own security
- Practicing an appropriate level of situational awareness
(These same three elements also serve to protect people against other crimes.)
In addition to becoming a hard target who is alert and difficult to surveil, potential tiger kidnapping victims should also employ good residential security measures and procedures to help persuade criminals that their home would be a difficult one to target successfully.
Obviously, the best outcome is to spot the criminals during their attack cycle and alert authorities so that they can be arrested.
But failing that, the secondary objective should be for the potential victim to become a hard target so that during the target identification phase of the attack cycle, the kidnappers will select another, more vulnerable target.
Prevention: Banks and other Businesses
Companies can also take steps to help prevent their employees from being targeted by tiger kidnappings.
In addition to providing training to employees on situational awareness, detecting hostile surveillance, and residential security, there are also some procedural measures that can be implemented.
Businesses should attempt to minimize the amount of cash or other valuables that can be accessed to the smallest amount required to operate.
They should also consider compartmentalizing valuables into smaller quantities and limiting an individual’s access to different compartments.
Instituting such a policy could help shield a business against tiger kidnappers who will divert to more lucrative targets.
Businesses should also take steps to limit sensitive information regarding business procedures and operations.
Such information should only be provided to employees with a need to know.
This can help make it more difficult for tiger kidnappers to get the intelligence they need on personnel and procedures.
Another step is to establish a system whereby two people must work in tandem to open containers holding valuables such as bank vaults and cash boxes.
This prevents any single individual from being able to turn the valuables over to the kidnappers and complicates the planning of tiger kidnappers.
Off-site control for opening critical locks or accessing large quantities of cash or other valuables can also be helpful.
Companies can also plan for tiger kidnappings by establishing special tiger kidnapping alarms and alarm procedures intended to protect employees and family members.
Such a program should contain verbal and non-verbal duress codes.
Obviously, implementing such procedures requires careful planning as well as training for employees and will vary by the type of business involved.
Companies are the ultimate targets of tiger kidnappers; employees are merely the vector used by criminals to target the company’s resources.
Because of this, most tiger kidnappings begin with criminals conducting surveillance at the company’s premises.
This allows companies to employ surveillance detection or countersurveillance teams at a location likely to be targeted.
Such efforts should be focused on times, such as opening and closing, when criminals would most likely be conducting surveillance against the location in an effort to understand operational procedures and determine which specific employee to target.
It is important to recognize that tiger kidnappers don’t just target bank employees.
They can also target people with access to jewelry stores, gun shops, warehouses, armored car companies, and other places that contain items of value.
Tiger kidnappers are a serious threat to a variety of businesses, but like any other kidnapping, they can be prevented by good security.
This report is the fifth in a series addressing different types of kidnapping and their motivations. The first part of the series, Understanding Kidnapping Threats, introduces different types of kidnapping. The second part, High-Value Kidnapping for Ransom, discusses how the required complex planning can be an advantage. The third part, Express Kidnapping, explores how these kidnappings do not follow the typical attack cycle. The fourth part of the series, Virtual Kidnapping, considers who the real victim is. The sixth and final part of the series, Crypto Kidnapping, centers on kidnappers who identify targets with large amounts of cryptocurrency.
